You follow the HIPAA checklist. You train your staff. But you're still not confident if your PHI is secure. Because legacy security just isn't built for how healthcare works today.
If you're responsible for securing patient data, you already know HIPAA compliance is more than a box ticking exercise. It requires strict safeguards, clear access controls, and proof that you're doing both-every single day.
But here's the challenge: most traditional security models (like perimeter-based defenses) weren't built for today's cloud-first, perimeterless environments. Users work remotely. Data moves across systems. And protected health information (PHI) exposure risks aren't just external, they come from inside too.
That's where zero trust comes in.
In this article, you'll learn how the zero trust security model, rooted in the principle of "never trust, always verify" aligns with HIPPA requirements. From access governance to breach prevention, we'll break down how this model gives you control over PHI while helping you stay audit-ready at all times.
HIPAA: The Most-Essential Compliance Regulation For The Healthcare Sector
What is HIPAA? Health Insurance Portability and Accountability Act aka HIPAA is a U.S. law enacted in 1996 to protect protected health information (PHI) from being disclosed without consent.
Also Read: Example Of PHI (Protected Health Information)
The rules and regulations of HIPAA are issued by the department of health and human services (HHS) and the office for civil rights (OCR) investigates whether covered entities are adhering to these rules & regulations.
Which entities are covered under HIPAA? Or can say who is actually required to comply with HIPAA?
Any organization that stores, accesses, and processes PHI or ePHI is obligated to comply with HIPAA, such as –
- Healthcare providers such as hospitals, nursing homes, and clinics.
- Healthcare insurance providers such as insurance companies, HMOs, and government programs like Medicare.
- Healthcare clearinghouse–institutions or individuals that act as intermediaries between providers and insurance companies to help process claims.
- Healthcare information exchange (HIEs)–organizations that help different healthcare providers exchange PHI.
- Organizations that dispose of hospital and patient personal records.
- Service providers, such as EHR (electronic health record) platform providers.
Additionally, associates such as lawyers, accountants, contractors, and IT specialists who access PHI are also required to comply with HIPAA.
But what rules and regulations must one follow to comply with HIPAA? Let’s find out.
The 3 Core HIPAA Rules
To comply with HIPAA, you as an organization need to meet 3 main rules: ‘privacy rule’, ‘security rule’, and ‘breach notification rule’.
Now that you know what rules need to be met, let’s find out how Zero trust security plays a role in helping you meet those rules.
How Zero Trust Security Helps Meet HIPAA Compliance?

Zero trust security model suggests:
- Never Trust, Always Verify: Every request to access PHI must be verified every time. Because, every identity, device, and application should be treated as untrusted – regardless of where they are located (inside or outside the network/perimeter)
- Implement Principle of Least Privilege (PoLP): Grant uses only the limited access necessary to perform their specific roles and responsibilities – nothing more, nothing less, reducing the risk of data misuse or exploitation.
Also Read: To learn more about PoLP, check out this blog post: What is the principle of least privilege (PoLP)?
- Continuously Monitor and Validate: Keep track of user behavior (how they are accessing PHI and what they are using it for), device health, and network activity.
This way, you can instantly detect and respond to any suspicious activity. Along with that, on a periodic basis, perform a review to detect access anomalies and address them before they create access gaps.
Also Read: The Essential Steps for Achieving a Zero Trust Security Model in Your SaaS Environment
This approach helps confidently meet the HIPAA privacy and security rule.
Note: Reporting a HIPAA breach to the affected party is solely your responsibility—Zero Trust has no role to play here.
Now, you’ll probably ask – ‘how to actually incorporate the zero trust security model into our strategy?’ Here’s how.
Steps To Incorporate Zero Trust Into Your HIPAA Strategy
Below, we’ve listed the steps-to-follow to incorporate the Zero Trust security model into your security setup.
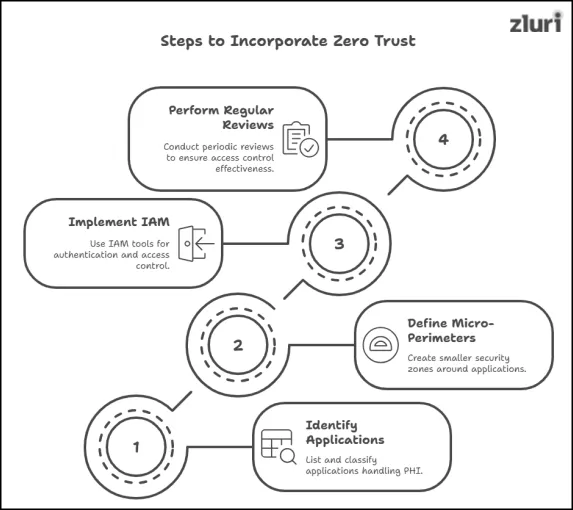
Step 1. Identify & Classify Applications
Start by:
- Identify all applications present within your environment
- List down the applications that store, process, or transfer critical PHI.
- Classify/categorize the identified apps based on the sensitivity of the data they hold and their importance to your operations.
This will enable you to prioritize your security efforts more effectively – making sure the most critical apps receive the highest level of protection and are governed properly.
Step 2. Define The Security Perimeter Around Applications
Up next –
- Replace Broader Perimeter With Micro Perimeter – Instead of setting up a broad network perimeter (simply put, security fence that separates trusted internal networks from the untrusted external ones), create micro-perimeters (smaller security zones) around individual applications that handle PHI.
- Treat Every Request As Untrusted – Even if the request for PHI access comes from within your own network, assume it's untrusted. So, every time a user tries to access an app that holds PHI, they have to prove they are authorized to access it.
Result? Even if one point of your system is infiltrated, the attacker cannot easily move to other areas (get access to other access-points) – keeping the damage limited.
Step 3. Leverage Identity And Access Management Tool To Authenticate, Authorize & Implement Access Control
Many IAM tools focus on just one or two areas – they can either help you authenticate your users or authorize them or help you implement access control.
But there is one advanced and intelligent IAM solution known as Zluri’s access management that helps meet all your needs.
- Helps Authenticate & Authorize: It integrates with IdPs such as Okta, Azure AD, AuthO, and others, to properly authenticate and authorize users before letting them access any apps that handle PHI.
- Helps Implement Access Controls: With Zluri, you don’t need to manually configure access controls for each application.
Instead, you can define access rules once using Zluri’s automation engine, and the system will automatically apply those rules across all integrated applications.
Suppose, if you want to allow access only to users in India who work for your organization, just define these context-based rules in Zluri’s automated workflow.
Step 4. Perform Reviews On A Regular Basis
To make sure the right users have the right access to the right app (that stores PHI) – over the time, you need to perform access reviews on a regular basis (quarterly, bi-anully, or annually, the more the frequency the better it is).
You can opt for Zluri’s access review solution for this purpose. All you need to do is–
- Select the applications that handle PHI
- Zluri automatically integrates with them to show you who currently has access. From there, you can easily identify:
- Unauthorized users who shouldn’t have access,
- Former employees or contractors who still hold permissions, or
- Users who no longer need access based on role changes.
To address detected anomalies – you can trigger Zluri’s deprovisioning or downgrade license playbook – no manual intervention needed.
Bonus Point:
By using Zluri to perform reviews, you can get valuable insight into the effectiveness of your access control strategy.
- If too many anomalies show up during review, it’s a sign your current policies may need tightening and adjustments.
- Refine your rules, make them stricter if needed, and ensure everyone complies.
This way, you can ensure the data is secure and successfully meet the requirements of HIPAA compliance (which is the ultimate goal).
Also Read: The HIPAA Compliance Checklist for 2025
Prevent HIPAA Violations & Security Breaches With Zero Trust
If you ignore to incorporate Zero Trust security model into your strategy, you may end up struggling to meet HIPAA rules.
This will not only jeopardize your chances of achieving HIPAA certification and expose you to HIPAA violation penalties, but will also increase the risk of encountering security breaches.
So, it’s better to take the right step today to avoid tomorrow’s headache of compliance and security implications.









.svg)



























.webp)







.webp)
.webp)





.webp)