Scaling fast doesn’t mean leaving doors open; yet that’s exactly what happens without automation.
As a tech company grows, so does its access sprawl. What used to be a manageable set of users and tools quickly turns into a tangled mess of identities, permissions, and workflows.
At 50 employees, it’s still possible (though inefficient) to track user access in spreadsheets and run manual reviews by chasing managers over email. However, by the time you reach 200 or 300 employees, with dozens of SaaS apps, rotating contractors, and multiple departments, manual access reviews become a significant liability.
They are time-consuming, error-prone, and completely disconnected from real-time changes in your environment. People join, switch roles, or leave, but their access stays. Managers approve reviews without context, simply to expedite the process. And when an audit comes around, your team struggles to understand what happened and why.
For high-growth companies, this isn’t just a compliance problem. It’s a security one. And without automation, you’re left filling gaps manually in a system that’s already ahead of you.
In this article, we will break down how fast-growing tech firms are building scalable, audit-ready access review processes, not by adding more manual effort, but by embedding automation into the way access is granted, reviewed, and revoked across their SaaS stack.
Why Manual Reviews Fail in Fast-Growth Environments?
For fast-growing tech firms, the gaps in manual access reviews don’t appear gradually; they widen all at once. When you’re onboarding 10+ employees a month, rotating contractors for specific projects, and adding SaaS tools to support new teams, your old access review processes quickly fall out of sync with reality.

Manual reviews aren’t just inefficient. They become a liability, both in terms of security and compliance.
1. Reviews scattered across spreadsheets, Slack threads & inboxes
Each team manages access differently. HR has employee start dates. IT handles provisioning. Security tracks reviews. But none of this is centralized, and certainly not automated. When it’s time for a quarterly access review, you are stuck pulling stale data from different systems, sending reminders manually, and reconciling conflicting inputs.
You lose precious hours just aligning on what access even exists, let alone whether it should be revoked.
2. Managers are asked to review access that they don’t understand
In theory, access reviews enforce the principle of least privilege. They become checkbox exercises. Why? Because most reviewers aren’t close enough to the access they are approving.
A sales manager might be asked to review a junior rep’s access to Salesforce, Gong, and five other tools, but they won’t know what specific permissions that rep actually needs day to day. There’s no usage data. No context about how the access was granted. So approvals become the default, not decisions.
This breaks the intent of access reviews: they’re meant to reduce risk, not rubber-stamp it.
3. Contractors, interns, and vendors become blind spots
Non-employees usually bypass your standard joiner-mover-leaver process. Their access is often provisioned manually, and rarely tracked in identity systems like Okta or your HRMS. Which means offboarding becomes a guessing game.
The result? A third-party developer who completed a project two quarters ago might still have access to GitHub or AWS. And no one knows until a misconfiguration or breach occurs.
These aren’t edge cases. For fast-scaling companies that rely on external contributors, they are the norm.
4. Leavers are offboarded from HR, but not from the tools they used
Even when HR marks a user as terminated, access doesn’t get fully revoked unless you have deep SaaS visibility. SSO might cover some core tools, but many departments add apps directly, especially in marketing, finance, or product, with no central control.
The problem is that IT teams lack a reliable method for detecting where access still exists. So offboarding becomes partial and inconsistent.
5. Audits become reactive, stressful, and messy
When the auditor asks, “Can you show us who had access to finance data last quarter, and have you reviewed it?” You realize you are not audit-ready. Instead of clicking a button, you spend days digging through email threads, outdated spreadsheets, and scattered approvals.
The issue isn’t just documentation; it’s the lack of a system that captures decisions in a verifiable and tamper-proof manner.
The real cost? You’re spending more time managing access reviews, but reducing the risk less. You’re scaling your teams and stack, but losing visibility and control. You’re aiming for compliance, but doing it reactively, under pressure.
Manual processes might have worked for 50 employees. But at 300? They’re not just inefficient; they're unsustainable.
What Fast-Growing Companies Automate & Why?
When access reviews start falling apart, fast-growing companies don’t try to fix them with more spreadsheets or reminders. They move towards automation, not just to save time, but to prevent risk from compounding as they scale.

Here’s what actually gets automated, and why it matters most.
1. Mapping user identities to actual access
The first step is visibility. Manual reviews often begin with someone asking, “Who even has access to this?” Automation eliminates that question.
By integrating with your identity provider (Okta, Google Workspace), HRMS (Rippling, BambooHR), and SaaS tools, companies create a live, unified access inventory. This includes:
- All active users (employees, contractors, vendors)
- Apps and systems that each user has access to
- Roles and permission levels across each system
- Whether access is tied to a specific role, team
This central view is foundational. Without it, you are reviewing blind.
2. Triggering reviews when access actually changes
Fast-growing companies move beyond static quarterly reviews. Instead, they set up event-driven triggers that launch reviews based on real activity:
- A user changes teams or departments
- A contractor’s end date is approaching
- Privileged access (e.g., admin to production systems) is granted
- An account hasn’t logged in for 30+ days
These triggers ensure that reviews happen at the moment of change, when risk is highest, rather than waiting for a review cycle.
3. Giving reviewers the right context to make real decisions
Automated workflows don’t just assign tasks; they make reviews actionable by enriching them with context. Instead of dumping a list of usernames, reviewers see:
- What apps does the user have access to
- What level of access they hold (e.g., admin, real-only)
- Last login activity or usage data
- Whether the access is standard for their role
- Who originally approved it
This transforms access reviews from rubber-stamping into genuine governance. Managers can make informed decisions without having to search across systems.
4. Revoking access directly from the review workflow
In a manual world, flagged access usually triggers a ticket to IT or a follow-up email to the app owner. That delay becomes a loophole; risky access remains open longer than it should.
Automated platforms let reviewers revoke access immediately, directly from the review interface. Once denied, the system pushes the changes through the provisioning layer (via SCIM, API, or native integrations), removing access instantly or notifying IT to do so.
5. Logging decisions for audit without manual effort
Every action, approval, denial, and justification is automatically logged and time-stamped. This creates a clean, auditable record:
- Who reviewed which user
- What decision was made
- Why was access retained or revoked
- When the review occurred
When it’s time for an audit, teams can export a complete evidence trail in minutes, not days. No need to search for Slack approvals or reconstruct decisions from email.
Why does this work? By automating these specific parts of the process, companies eliminate guesswork, reduce review fatigue, and stay ahead of compliance requirements, without slowing growth or overwhelming security teams.
What Does this Look Like in Practice?
Automation isn’t just a future-state concept. Fast-growing tech firms are already utilizing it to manage sprawling access environments, doing so in a manner that scales with their growth.

Here’s what these workflows actually look like inside modern IT and security teams:
Case 1: HR triggers a review, and IT doesn’t miss a step
An employee moves from Marketing to Product. That change is pushed from the HRIS (say, BambooHR) to the identity provider (like Okta) and automatically triggers a mid-cycle access review.
The system flags that the user still holds “Editor” access in Canva and a paid Zoom license, both of which are irrelevant to their new role. The manager reviews the suggestions with the usage data in hand, sees no activity in 45 days, and revokes the access with a click.
Result? No manual handoff. No delays. Access is adjusted before it becomes a problem.
Case 2: Contractors offboarded, without manual tickets
A group of contractors wrapped up a 90-day customer support initiative. Their end date is captured during onboarding and tied to their accounts across Zendesk, Slack, and Google Drive.
As the end date approaches, the system runs an automated review, surfacing these accounts to the manager with pre-filled revocation options. Once confirmed, access is terminated across all assigned tools via native integrations.
Result? No open tickets. No forgotten users lying in your support systems.
Case 3: Review cycles that fit into your workflow
Quarterly access reviews used to mean pulling spreadsheets from six tools, emailing managers, and chasing down approvals. Now, reviews are pre-scheduled and auto-generated.
Each reviewer gets a clear, role-based list of their direct reports’ access, usage insights, and recommended actions, delivered via email or within the platform. Approvals and revocations happen in-platform. All decisions are logged automatically.
Result? Reviews take hours, not weeks, and actually reduce risk instead of just checking a box.
Case 4: Compliance teams export audit logs in minutes
An auditor requests evidence of access review cycles for your finance systems. Instead of chasing emails and building screenshots, the compliance lead logs into the platform, filters by application and time period, and exports a complete log:
- Who reviewed which users
- What decisions were made
- Justifications, timestamps, and revocation records
Result? No panic, no ad hoc documentation, and no findings during the audit.
These aren’t hypothetical improvements; they are real operational gains. By embedding automation into access governance, growing tech firms make it easier to do the right thing: review access regularly, remove it when it’s no longer needed, and prove it all when asked.
And critically, they do it without adding headcount or slowing down growth.
What to Look for in an Automated Access Review Platform?
Not all automated access review platforms are designed for fast-moving tech firms. Many are repackaged legacy systems or compliance-first tools that hinder productivity with rigid workflows, complex integrations, or a lack of real-time context.
If you’re scaling fast, onboarding dozens of employees per quarter, integrating new SaaS tools weekly, and preparing for audits quarterly, you need a platform that adapts to your pace and tech stack.
Here’s what to prioritize:
1. Integration depth with your SaaS stack
Access reviews are only as accurate as the data you can pull in. You will need real-time context on who has access to what and why.
Look for a platform that:
- Natively integrates with your identity providers (like Google Workspace or Azure AD), HRMS, finance, and your most sensitive apps (e.g., Salesforce, GitHub).
- Support multiple app instances, especially when operating across regional workspaces or M&A environments.
- Surface role metadata and user attributes from connected systems so reviewers get the complete picture (e.g., joining date, department, employment status).
Note: Beware of tools that claim “integration” but only export CSVs or rely on ITSM tickets to process revocations.
2. Automation that goes beyond scheduling
Many platforms can schedule reviews. However, few can truly automate the entire lifecycle, encompassing data collection, review, remediation, and audit.
Choose a platform that:
- Triggers reviews automatically based on specific events, such as employee termination or department changes.
- Assign reviewers based on role, reporting manager, or app ownership.
- Remove access directly in integrated apps, not by routing everything through IT tickets.
- Logs every action taken from review access decisions to revocations for complete audit trails.
3. Context-rich reviews that speed up decision-making
A major reason reviews get rubber-stamped is that reviewers often lack the time or necessary context to make informed decisions.
Your platform should:
- Highlight risky access (e.g., external users, stale accounts, admin roles).
- Group access intelligently (e.g., show unused permissions)
- Offer access and usage details like last login, department, or why a user has access
- Allow delegation or fallback reviewers to prevent reviews from getting stuck.
4. Remediation workflows that actually remove access
Spotting unnecessary access is only half the job. If your platform stops at “review complete” and leaves revocation in a backlog, you are not solving the problem; you are just moving it.
Look for:
- Built-in access revocation for all integrated apps.
- Bulk remediation options, where reviewers can remove multiple entitlements with one click.
- Automated follow-ups for skipped or delayed actions.
- Audit-ready evidence showing what was removed, by whom, and when.
5. Scalability and future readiness
What works for 100 employees may not work for 1000. Choose a platform that doesn’t just solve your problems today, but can support a roadmap toward broader identity governance.
Consider platforms that also offer:
- Self-service access requests with approval routing.
- Lifecycle management for automating onboarding/offboarding.
- Segregation of duties (SoD) enforcement and role-based access control (RBAC).
- Customizable review policies across apps, departments, and access types.
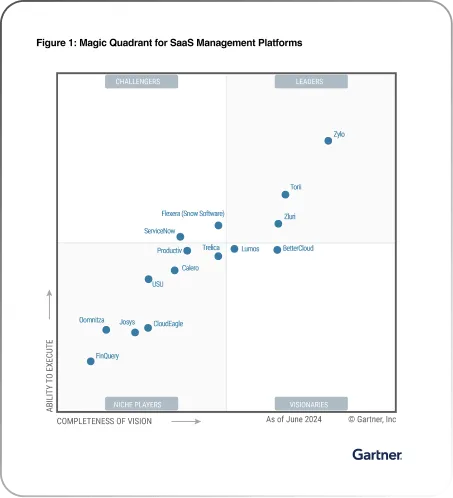
How Zluri Helps Fast-Growing Tech Firms Automate Access Reviews?
Fast-growing tech companies often find themselves managing an exploding SaaS stack, onboarding and offboarding employees across geographies, and dealing with increasing access risk. Zluri fixes all by offering the following capabilities.
1. Complete SaaS visibility
Zluri’s discovery engine automatically uncovers all SaaS apps in use, including shadow IT and apps not connected to your SSO. This addresses a critical gap that most access review tools overlook: the fact that a significant portion of app usage in mid-sized and fast-growing companies bypasses formal IT provisioning.
Even for apps that don’t support SCIM, Zluri still presents user and access data, giving IT teams visibility into every account, whether it is tied to Okta, Google Workspace, or provisioned manually.
You also get visibility into:
- Third-party contractors, vendors, and interns
- Shared accounts and service accounts
- Orphaned users who were never deprovisioned
This enables IT to conduct access reviews across all user types, without being hindered by integration gaps or app ownership issues.
2. Out-of-the-box integrations for your entire SaaS ecosystem
Zluri supports over 300 out-of-the-box integrations across collaboration, finance, engineering, marketing, HR, and security tools. These integrations go beyond surface-level metadata; they pull deep contextual access data, like:
- Workspace and project-level access (e.g., specific boards in Trello)
- Role and license tiers (e.g., admin vs viewer, basic vs pro)
- Usage activity (e.g., last login date, app actions)
Unlike platforms that assume one app = one instance, Zluri supports multiple instances of the same application. This is critical for tech firms operating across business units or regions with isolated app configurations.
Also, Zluri allows you to:
- Send secure connection links to app owners for delegated integration
- Configure authoritative sources if identity data lives in multiple systems (e.g., HRIS, ITSM, IdP)
This flexible data model ensures technical limitations don’t bottleneck your access reviews.
3. Closed-loop access remediation that actually resolves risk
Where most UAR tools stop at flagging issues or sending emails, Zluri enables automated remediation directly from the review workflow, eliminating the need for tickets.
During campaign setup, IT can pre-define what should happen when access is marked for removal:
- Revoke access entirely
- Downgrade user roles (e.g., admin to read-only)
- Adjust license plans (e.g., pro to basic)
- Modify granular permissions (e.g., remove access to private Slack channels)
These actions are executed directly via API through Zluri’s integration, so reviewers don’t need to chase other teams or wait for access IT ticket resolution.
For example:
- A contractor who hasn’t logged into GitHub for 60+ days is automatically flagged and removed
- A product manager with admin access to the finance dashboard is downgraded to a viewer
- Users with premium Zoom licenses who haven’t hosted a meeting in 3 months are downgraded to basic
This approach improves time-to-remediation, reduces risk, and reduces unused license costs.
4. Risk-based insights to prioritize what actually needs review
When tech firms scale fast, reviewers can easily become overwhelmed with access decisions. Zluri uses intelligent recommendations to help teams focus on what matters most.
Key risk signals include:
- Dormant users: Users with access but no activity in the app for 30+ days
- Privilege anomalies: Users with unusually high access compared to peers in the same department or role
- External identities: Third-party vendors or interns with persistent access beyond engagement periods
- Sensitive app access: Accounts with privileged access to financial, code-based, or PII systems
Rather than expecting approvers to manually analyze every row, Zluri helps reviewers prioritize by highlighting these issues upfront, providing clear reasoning and recommended actions.
This reduces rubber-stamping and ensures risk decisions are informed, not reactive.
5. Configurable multi-level workflows that fit your organization's structure
Access decisions in growing organizations often require approval from multiple stakeholders. Zluri supports completely configurable multi-level approval chains based on:
- App sensitivity
- User type (internal vs external)
- Business unit or geography
Example flow for critical finance tools:
- Functional manager: Confirms business need
- IT or security reviewer: Validates role/permission risk
- Compliance officer (optional): For regulated data, e.g., payroll or tax records
These workflows are built directly into the campaign, so you don’t need to coordinate over email or Slack. Zluri automatically routes reviews, sends reminders, and tracks every approval, creating a verifiable audit trail.
You can also set:
- Escalation rules for overdue approvals
- Reviewer delegation
- Conditional logic for different user/user types
6. Always audit-ready, without the manual work
Zluri simplifies audit prep by giving you:
- Detailed access review logs: Who approved what, when, and why
- Remediation records: Including revocation or license downgrade details
- Campaign history: Evidence of reviewer decisions and reminders
- Exportable reports: For SOC 2, ISO 27001, HIPAA, and other frameworks
Everything is tracked and reportable with just a few clicks, eliminating the need for spreadsheets and the rush to meet audit deadlines.
Why do fast-growing tech firms choose Zluri?
Zluri stands out in high-growth environments because it:
- Doesn’t assume every app is SSO-enabled or SCIM-compliant
- Works across distributed teams and hybrid SaaS ownership models
- Goes beyond review with real-time remediation and cost optimization
- Offers deep integration coverage with minimal IT interference
- Helps meet compliance requirements without slowing down growth
With Zluri, access reviews aren’t just a checkbox; they become an always-on control that improves security posture, reduces SaaS waste, and scales with your team.
Book a personalized demo to see how Zluri helps fast-growing tech firms automate access reviews and compliance.
Automate Access Reviews Today to Protect Tomorrow’s Growth
Access reviews aren’t just a checkbox for compliance; they are a control surface for your entire security posture. As your company grows, the cost of mismanaging access isn’t measured in lost productivity or late audits; it’s measured in exposed data, dormant admin accounts, and doors left open.
The most forward-thinking tech companies treat access reviews not as a quarterly ritual, but as a continuous, embedded part of their identity, risk, and change management. They use automation not to replace humans, but to amplify their judgment by surfacing the right context, triggering reviews at the right moments, and enforcing decisions immediately.
If you’re still debating when to automate, the answer is simple: before things become worse. At scale, the gap between knowing and acting is where most risk resides. Close the gap now, and your future team will thank you, not just for compliance, but for the control it provides.
Also Read: User Access Review Procedure









.svg)



























.webp)







.webp)
.webp)





.webp)