Think about the last time someone left the company,
The old perimeter is gone. In a SaaS-first, remote-friendly world, the traditional notion of a network perimeter is all but gone. Your users log in from everywhere. Your data lives across hundreds of apps. And your security posture relies on a single control point: identity.
Identity-first security is now the strategy. What used to be an access policy is now the anchor of enterprise security. But identity-first security isn’t just about SSO or MFA. It’s about governing who has access, when, why, and for how long.
The reality? Most IT teams still struggle. Why?
- Access data is scattered across your identity provider (IdP), HR information system (HRIS), and individual Software-as-a-Service (SaaS) applications.
- Revocations get delayed.
- Contractors often retain access to the app after their projects are completed.
- Review cycles become checklist exercises. And when audits come around, there’s no clear trail to show who approved what, and why.
That’s where identity governance and administration (IGA) comes in. IGA has quietly become the backbone of a modern security framework. It’s how IT teams regain visibility, enforce least privilege, and respond to threats before they escalate.
And the cost of inaction is rising. How? According to IBM’s 2024 Cost of Data Breach report, stolen or compromised credentials remain the leading cause of breaches, with an average cost of $4.9 million per incident (a 10% increase over the last year and the highest total ever). In a world where identity is the new perimeter, IGA is no longer optional.
In this article, we will explore how IGA evolved from a behind-the-scenes process to a frontline security control, and why it’s now vital for organizations to adopt identity-first security.
A Quick Look Back: Why Traditional Security Models Fell Short?

Before identity became the centerpiece of modern cybersecurity, organizations leaned on perimeter-based security. Firewalls, VPNs, and endpoint protection were the go-to tools, designed for a world where users worked from office networks, apps were hosted on-prem, and IT teams controlled every layer of infrastructure.
However, that model didn’t last long.
SaaS adoption exploded. Workforces became remote, distributed, and more dynamic. Users started adopting tools outside official IT channels. As a result, the traditional perimeter crumbled, and so did the visibility and control that came with it.
Security teams suddenly faced blind spots everywhere. They no longer had clear insights into what apps were being used, who had access to them, or how that access was being governed.
IAM tools helped authenticate users and secure logins, but that wasn’t enough. Organizations needed a new way to manage access risk in this SaaS-first, perimeter-less environment.
Why IAM Alone Isn’t Enough for Identity-First Security?
Identity and access management tools, with their subsets such as SSO and MFA, have become increasingly essential as SaaS and remote work tools continue to gain popularity. They solved a key problem, authenticating users quickly and securely across applications.

But IAM was never designed to govern access.
It doesn’t show you:
- Who has access to what resources
- Whether that access is still needed
- Who approved it, or was it ever reviewed
And it doesn’t support:
- Consistent deprovisioning across SaaS apps
- Risk-based decision making
- Time-bound or contextual access
As a result, access gets provisioned but rarely re-evaluated. Former employees and contractors retain entitlements. Review cycles become spreadsheet-driven exercises that lack real context. That’s where the real risk lies, and that’s why IGA became necessary.
But addressing these challenges requires more than just managing identities. It demands a shift in mindset and practice. This is where identity-first security comes into play. Rather than focusing solely on authentication, identity-first security centers on governing who has access, what they can do, and when that access should be granted or revoked.
Identity-First Security in Practice: What it Looks Like Today?
The term' identity-first security' is used a lot, but what does it mean in practice?
At its core, identity-first security flips the traditional model: instead of building protections around your infrastructure, you build protections around who is accessing it. Every user, every machine, every integration becomes an identity, and every identity is a potential attack surface.
In today’s SaaS-first, perimeter-less environment, this approach isn’t optional. It’s how modern organizations manage access risk at scale.
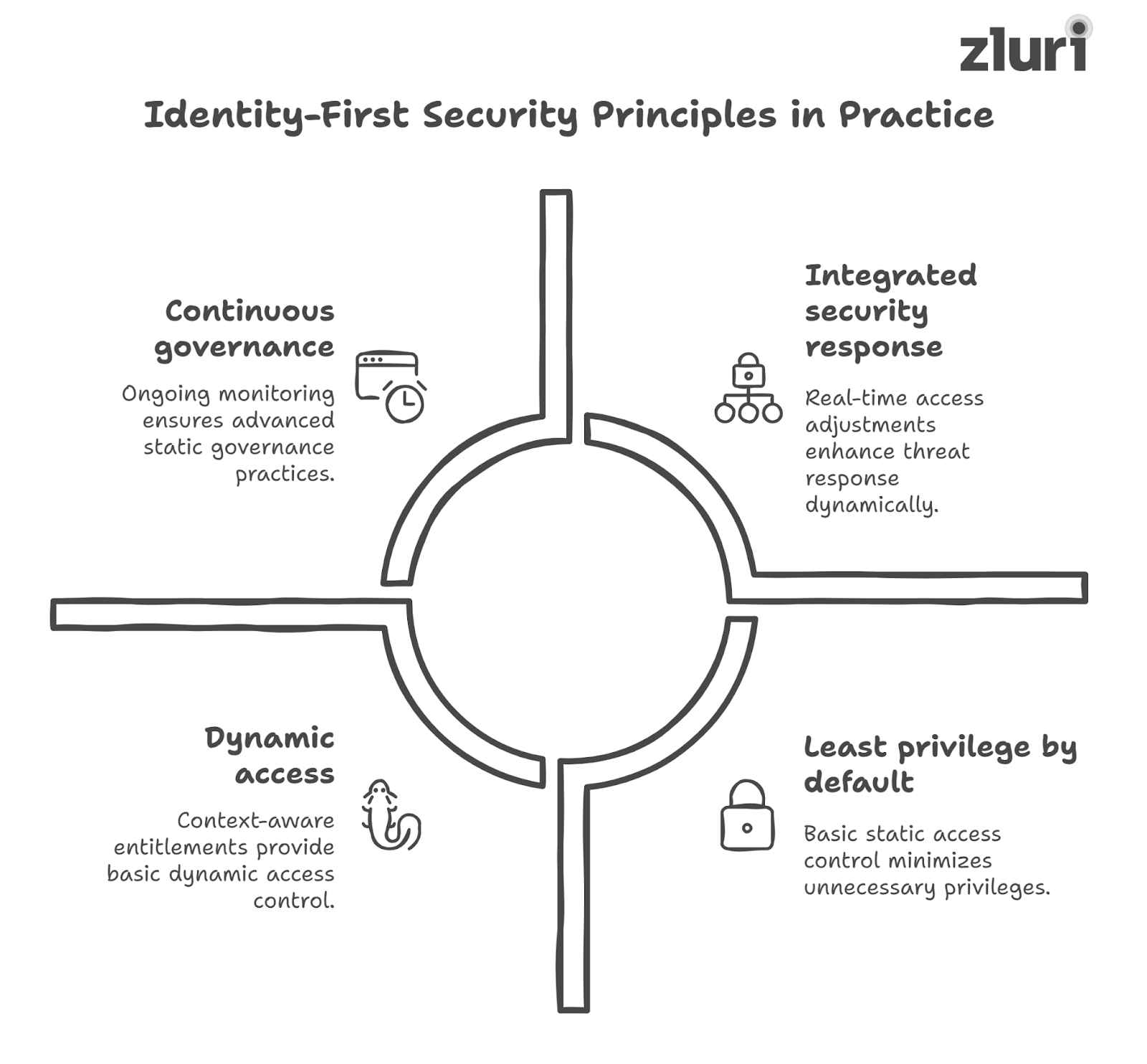
Here’s what identity-first security looks like today:
This shift demands more than identity infrastructure; it demands identity governance. And that’s exactly where modern IGA tools come in, evolving to become a strategic pillar of your security framework.
The Rise of IGA as a Strategic Security Control
Identity governance and administration began as a tool primarily focused on compliance, ensuring organizations could prove who had access to what, and that access was revoked when employees left. It was often siloed within IT or GRC teams and treated as a periodic, checkbox exercise.
However, as identity became the new perimeter, the role of IGA underwent a dramatic transformation.
Today, IGA is a core component of modern cyber strategy. It’s no longer just about ticking compliance boxes; it’s about actively managing and reducing access risk across the entire SaaS stack.

Here’s how IGA stepped up to this strategic role:
- Visibility beyond authentication: Unlike IAM systems, which verify identity, IGA tools provide deep insights into who has access to what across all SaaS applications, service accounts, and non-human identities. This visibility is critical to enforcing least privilege and detecting access sprawl before it becomes a risk.
- Continuous, risk-based governance: Modern IGA solutions automate access reviews, enforce time-bound entitlements, and trigger remediation workflows based on risk signals. This continuous approach replaces the manual, once-a-year review cycle with an ongoing, adaptive security posture.
- Bridging IT and security: IGA unites IT operations with security teams, enabling coordinated governance policies that align with threat intelligence, compliance mandates, and business goals. Security leaders now view IGA as an anchor rather than a back-office function.
- Reducing breach risk and insider threats: By maintaining control over access, IGA tools reduce the attack surface available to malicious actors or careless insiders. This capability directly impacts breach prevention and limits potential damage.
- Accelerating audit readiness: Automated tracking of access changes, approvals, and remediations creates an auditable trail that simplifies compliance reporting, saving time and effort during regulatory audits
- Scaling with complexity: As organizations adopt more SaaS applications, support remote and hybrid workforces, and manage non-human identities such as bots and APIs, IGA scales governance effectively, preventing access drift that IAM alone cannot prevent.
In short, IGA has evolved from a compliance checkbox to a strategic, proactive control layer, one that emphasizes identity-first security and strengthens your entire cybersecurity posture.
To truly appreciate this transformation, let’s compare how access governance looked before modern IGA and what it looks like now with today’s solutions.
The Old Way vs The IGA Way
Before modern IGA solutions, managing access was a slow, error-prone, and manual process. IT teams struggled to keep up with the growing complexity of SaaS environments and the evolving work environment.
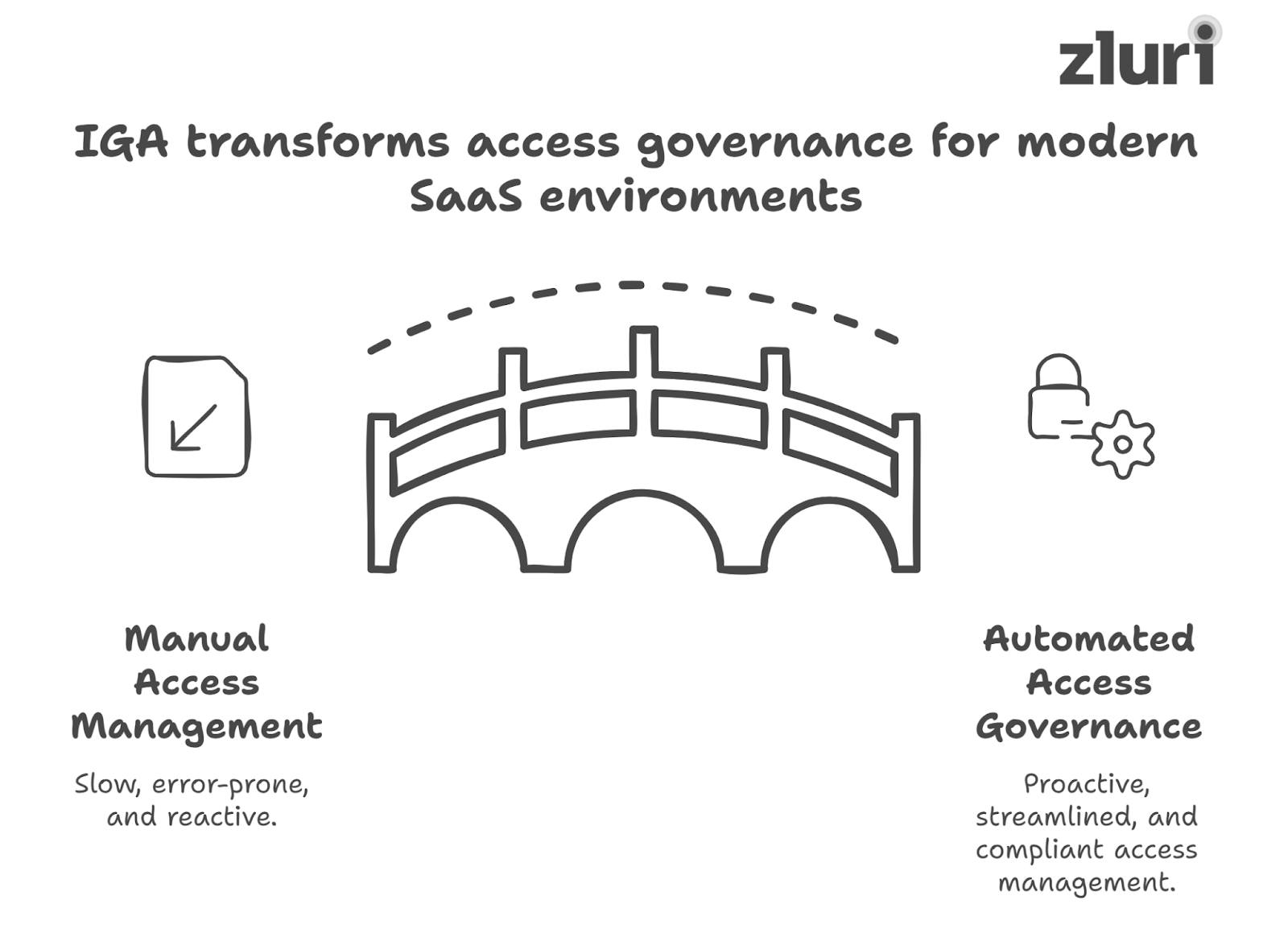
Understanding how modern IGA transforms access governance is one thing, but seeing how these principles come to life in a real-world solution is another. That’s where Zluri steps in. Built from the ground up with identity-first security in mind, Zluri’s approach to IGA delivers the capabilities today’s organizations need to gain visibility, automate governance, and proactively manage access risk across their SaaS stack.
Zluri’s Approach to Identity-First IGA
Legacy IGA tools weren’t built for the SaaS-first world. They were reactive and took months to implement. Zluri, on the other hand, takes a different approach, designed to meet the needs of modern, identity-first security.
Here’s how zluri embodies the principle of identity-first IGA:
1. Seamless integrations across your stack
Before you can govern identities, you need to know exactly who has access to what. And that means connecting to every app and system in your environment. Zluri’s native iPaaS engine makes this easy. It integrates not just with your core systems, such as IdPs and HRMS, but also with third-party apps, custom tools, on-premise infrastructure, developer tools, SCIM apps, non-SCIM apps, or any other apps present in your tech stack.
It offers over 300 prebuilt integrations with popular SaaS and cloud apps, allowing you to easily connect these apps to Zluri without writing any code. It also offers a Software Development Kit (SDK) for building custom integrations, even when APIs are limited or restricted to enterprise tiers. Thus, it provides flexibility and control, even for hard-to-integrate apps, by allowing you to write custom code to precisely control how data is sent and received.
This wide coverage means Zluri doesn’t just pull identity data from one source; it cross-correlates it across systems, removing blind spots and giving you the complete context of every user and app relationship.
Why does it matter? Identity-first security requires complete, continuous visibility. Zluri’s integration-first approach ensures that no app or identity is left out: shadow IT, AI tools like ChatGPT or Claude, unfederated apps, and even non-human identities, such as service accounts, are all accounted for.
2. Allows you to apply access control to restrict access to critical applications
Once you know which apps need protection, your team can use Zluri’s automation rule engine to control exactly who can access those applications and when. Here’s how it works:
This workflow can be triggered either during user onboarding or when an admin requests access. Zluri automatically applies these rules, ensuring that only authorized users from the correct department and role receive access, with no exceptions or guesswork.
Why does this matter? By strictly limiting access to authorized users, you reduce the risk of data misuse or unauthorized exposure. Sensitive financial data stays protected because access is never “just in case,” it’s precise and aligned with your security policies.
3. Performing access reviews to detect anomalies
Controlling access is just one part of the story. You also need to verify that these controls are working as expected. Zluri’s access review solution simplifies this by automating your access reviews.
Here’s what you do:
- Specify the application that you want to review.
- Zluri will automatically list the users who currently have access to those apps, along with key attributes such as their department, activity status (active or inactive), role, and more.
- With these insights, your team can easily verify whether access has been granted only to authorized users.
If, during the review, your team detects anomalies such as inactive users, former employees, or non-adminis with access to critical apps, it is a sign that the access controls require improvement. Maybe some permissions weren’t revoked properly, or roles have changed, but access wasn’t updated.
4. Automating remediation with playbooks
Here’s the best part: You don’t have to fix these anomalies manually. Zluri comes with configurable deprovisioning license playbooks that automatically revoke or modify access permissions when triggered. This means:
- Access for inactive or unauthorized users is promptly removed
- Permissions can be downgraded to a safer level, if needed
- No manual intervention is required, freeing up your team’s time and reducing human error
The impact? By regularly detecting and automatically fixing access anomalies, you reduce the attack surface. You close gaps that attackers might exploit and maintain ongoing control over who can access your critical business apps.
With Zluri’s identity-first approach to IGA, you get a proactive and automated way to govern access. One that enforces the least privilege, zero-trust principle, and continuous compliance. This isn’t just about ticking boxes; it’s about ensuring the right people have the right level of access at the right time.
Identity-First IGA Isn’t Optional, It’s Your Competitive Advantage

Securing identities isn’t just about blocking threats. It’s about giving your team the clarity and control to move fast, without putting the business at risk.
With identity-first IGA, you are not just checking boxes for compliance. You are ensuring that every decision – who gets in, for how long, and why – is intentional. You’re aware of risks early and close gaps before they become major issues.
As your company grows –with more apps, more users, and increased complexity – identity governance helps you stay in control without slowing things down.
The result? Stronger security, smoother operations, and a setup that scales with you.
That’s the real value of putting identity first.









.svg)



























.webp)







.webp)
.webp)





.webp)