Healthcare runs on trust. Ransomware runs on access. And right now, attackers are breaching that trust by hijacking credentials, exploiting misconfigurations, and encrypting critical systems. The cost? Patient care, reputation, & compliance.
According to the BlackFog State of Ransomware 2025 report, the healthcare sector faced a record-breaking 278 ransomware attacks in Q1 alone—a 45% spike from the last year. What’s even more concerning is that each month in Q1 2025 broke previous records, culminating in 107 attacks in March alone, the highest ever reported.
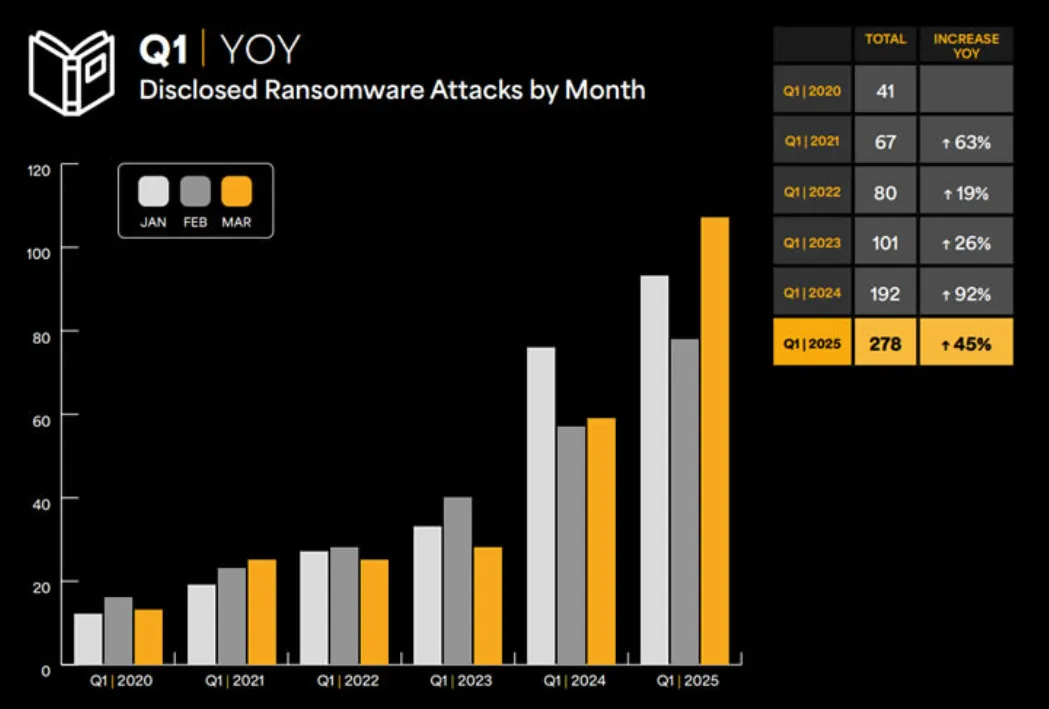
Even one of the ransomware attacks in 2025 made national headlines.
On May 20, 2025, Kettering Health (a major healthcare system in western Ohio with 14 medical centers and 120 outpatient facilities) experienced “a system-wide technology outage” that affected all 14 of its medical centers and brought its call center operations to a halt.
According to CNN, the ransomware attack was carried out by the Interlock ransomware group, which is known for its double extortion attacks on the healthcare sector. The ransomware group infiltrated Kettering’s networks, identified the data of interest, exfiltrated files, and then used ransomware-as-a-service to encrypt files.
They demanded payment of the ransom to prevent the stolen data from being published on their dark web leak site and to secure the decryption keys needed to restore access to the data.
You might be thinking, why is healthcare under siege? And what makes it such a prime target for ransomware groups? Let’s find out.
Key Reasons Why Healthcare Is Being Targeted
Here’s why healthcare is facing ransomware attacks:
Now — “Why are ransomware attacks able to infiltrate systems? It’s because healthcare organizations have the following loopholes:
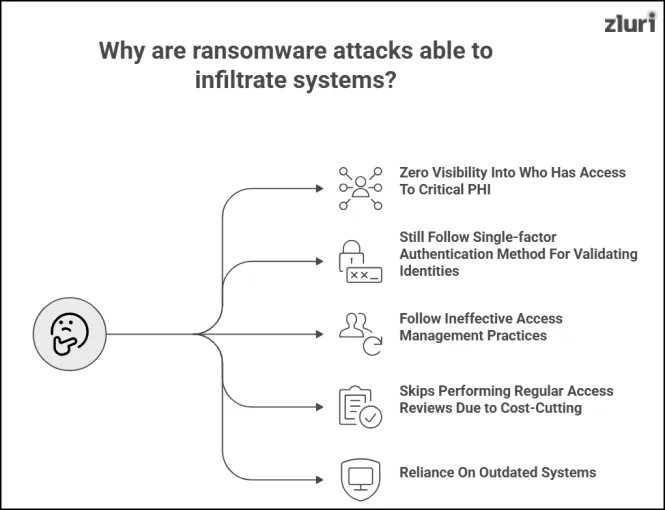
1. Zero Visibility Into Who Has Access To Critical PHI
In today's healthcare facilities:
- A wide variety of apps are used daily to process, store, and transmit sensitive PHI.
- These tools are accessed by a large and constantly changing workforce, including doctors, nurses, administrative staff, and third-party vendors.
Due to this, organizations struggle to track down who has access to apps that hold PHI. Additionally, neither of them has the right tool in place to achieve this visibility.
Result? Unauthorized users and orphaned accounts that retain access to critical PHI often go undetected – and attackers target these accounts, exploit them, and move laterally through the network perimeter.
2. Still Follow Single-factor Authentication Method For Validating Identities
Believe it or not, many facilities still depend on a single-factor authentication method to validate whether a user is legitimate.
What’s the problem? It’s simply not enough.
Cybercriminals can easily exploit this weak defense by either guessing simple credentials or stealing login details through phishing attacks or data leaks. Once they have access, they can slip right in undetected.
3. Follow Ineffective Access Management Practices
In the rush to save time, many healthcare facilities use group-based provisioning, where entire user groups are granted access to multiple applications simultaneously.
The problem is – even users who don’t need access to certain apps still get it; just because they’re part of the group.
Over time, these users accumulate unnecessary permissions, creating access gaps that cybercriminals can exploit. Attackers target these gaps to access more applications that hold sensitive PHI.
4. Skips Performing Regular Access Reviews Due to Cost-Cutting
Many healthcare facilities avoid regular access reviews to save money. However, skipping them means overlooking access anomalies and giving attackers more opportunities to exploit those gaps and move undetected through the system.
5: Reliance On Outdated Systems
Most healthcare organizations still rely on legacy security management systems that lack the latest security patches or have weak security controls. These outdated systems often create security gaps that allow cybercriminals to sneak in and easily access internal networks.
Best Practices to Close Identity Governance Gaps That Enable Ransomware Attacks
Below, we’ve listed the key best practices to follow to strengthen identity governance and shut down ransomware entry points.
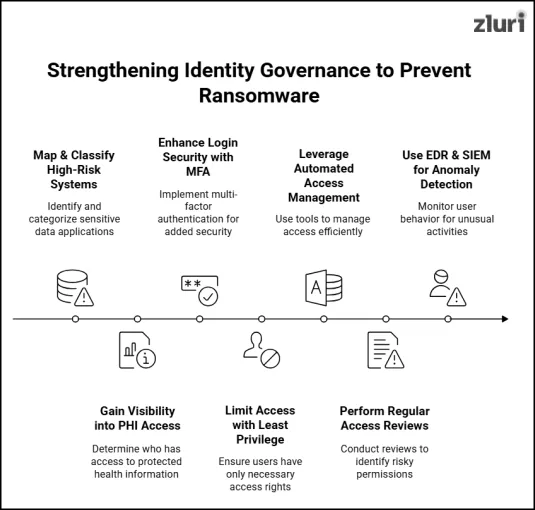
1. Map & classify high-risk systems & applications to enforce identity controls
- Start by finding the apps that store highly sensitive data (that must never be disclosed) – like electronic health records (EHRs), billing systems, telemedicine applications, and others.
- Classify these apps based on the sensitivity of the data they store, process, or transfer.
This will help you prioritize which apps need more protection, and accordingly, you can implement strict security access control to prevent unauthorized users from accessing them.
2. Gain visibility into who has access to PHI
You can leverage Zluri’s discovery engine to identify which identities (whether internal, external, or service accounts) have access to your PHI.)
Once you have this visibility, you’ll be able to figure out who should and shouldn't have access to the PHI.
3. Enhance login security by implementing multi-factor authentication
Instead of relying on single-factor authentication, implement multi-factor authentication, which will act as an additional layer of security.
- Even if an attacker somehow manages to obtain a user's password, they will still be required to provide an additional form of verification – such as a one-time code (OTP), biometric input, or FIDO2/YubiKey, which they typically won’t have access to.
This extra step will strengthen your defense mechanism, making it extremely harder for attackers to break in and much easier for you to keep sensitive patients’ data safe.
How to implement MFA?
- You can leverage tools such as Okta Adaptive MFA, Microsoft Entra ID, and IBM Verify.
4. Limit access with least privilege & segregation of duties
So, to stop attackers from taking advantage of over-privileged accounts, you need to do the following
- Implement the principle of least privilege: This practice will help ensure that every staff member or workforce member only has the minimum level of access required to perform their duties - nothing less, nothing more.
Now, even if attackers manage to gain access to a staff member’s accounts, they’ll have limited access to the systems and cause less damage.
- Enforce segregation of duties: This practice ensures that no single user has end-to-end control over critical processes.
How to enforce PoLP & SoD?
To implement PoLP:
- You can use an access control list (ACL) to define who can access which healthcare resources, what actions they can perform, and what actions they cannot perform.
- Or else leverage Zluri’s access management tool. You simply need to specify conditions in the automation rule workflow, and Zluri takes care of the rest – enforcing the rule across the organization.
- To enforce SoD, you can create access control policies and specify the user’s roles and responsibilities.
5. Leverage the automated access management platform to effectively manage identity’s access
You can leverage Zluri’s access management to effectively control your identity’s access.
- It doesn’t follow group-based provisioning; instead, it automatically grants identities access to applications relevant to their role, eliminating the risk of unnecessary app access accumulation.
- Similarly, it automatically revokes access of users whenever a user departs from the organization or transitions to a new role, preventing the creation of orphaned accounts.
6. Perform regular access reviews to flag risky permissions
Performing regular access reviews helps determine whether users have appropriate access to applications that hold PHI.
However, manually carrying out access reviews can be costly. So what you do instead is leverage Zluri’s automated access review solution (you can use it to perform micro-access review multiple times).
Here’s how it works:
- Simply select the app you want to review.
- Zluri integrates with it and shows you which users have access.
- It highlights contextual risk insights factors, such as privileged accounts, inactive users, ex-employees, and more.
Act on what you find:
- Use these insights to verify the validity of access.
- If anomalies are spotted, run Zluri’s deprovisioning and downgrade license playbooks to revoke or modify access instantly.
Plus, by performing this review, you will get clarity on whether your security strategy, access control, and policies are working effectively or not. More access anomalies indicate a gap in your strategy, and you need to make improvements.
7. Use EDR & SIEM to detect anomalies, but don't rely on them alone
Strong identity governance helps you control who can access what. But what about how access is used in real-time? That's where EDR and SIEM tools step in.
These solutions monitor user behavior, detect anomalies (such as unusual login times or access patterns), and alert your team before attackers can escalate their activity.
Note: Use them together. Identity governance narrows your exposure, while EDR and SIEM provide visibility into potential misuse or credential compromise as it happens.
Strengthen Identity Governance Before You Become the Next Headline
With ransomware attacks surging, healthcare facilities have no choice but to strengthen their identity governance.
Every over-privileged account, every orphaned access, every ignored security control — it’s an invitation for trouble.
If you don’t act now, you're not just risking patient care disruptions or regulatory penalties – you’re gambling with your reputation. So, act today to avoid tomorrow's trouble!






.svg)


























.webp)







.webp)
.webp)





.webp)