Identity governance and SaaS management platforms are the two most widely used solutions in today’s cloud-first world. While both directly/indirectly manage identities and applications, they are built to solve different core problems. In this article, we’ll take a closer look at what sets identity governance vs SaaS management platforms apart.
Every organization battles its own version of chaos; it encounters different sets of challenges periodically.
- Some struggle to control and manage SaaS application sprawl,
- While some aren’t able to prevent access misconfiguration (unable to prevent wrong identities from having critical access).
These are just surface-level issues that organizations aim to resolve.
But more often, there’s a web of hidden problems lurking beneath the surface – ones that don’t show up until it’s too late (when data already gets exposed, unnecessary SaaS costs spike up, or frequent audit fails take place).
To address these issues, identity governance and SaaS management platforms play a crucial role. But what specific problems do they solve, and how do their methodology differ?
Let’s find out.
Comparing The Problem-Solving Scope Of Identity Governance vs SaaS Management Platforms
Below, we’ve differentiated identity governance vs SaaS management platforms based on what problems they help address and how they do it.
Identity Governance Platform: A Solution Designed To Control Who Gets Access To What & When
An identity governance platform is a purpose-built solution that helps ensure the right users have the right access to the right resources, and at the right time.
What problems does it help resolve?
It addresses three main problems:
- Identity security risks
- Compliance gaps/risks
- Operational inefficiencies
It tackles nearly every possible problem that one can encounter while managing the joiner-mover-leaver cycle, access requests, and access certification.
List Of Common Problems Organizations Face During JML Cycle Management & How Identity Governance Platform Helps Address Them
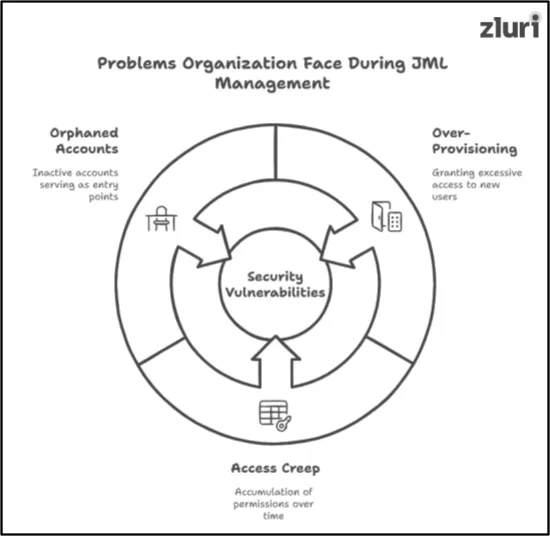
1. Over-Provisioning
In many organizations, IT teams tend to grant new joiners more application access than they require. They assume that the user will eventually need that access.
However, this approach often results in over-provisioning (introducing unnecessary risk by expanding the attack surface).
How does IGA address it?
Identity governance solutions solve this issue by allowing your team to trigger automated provisioning role-based workflows.
- These automated workflows ensure that users receive access to applications that are required for their role only – nothing more. This reduces the attack surface and protects your critical data from being exposed/leaked.
- In fact, since the solution automates the end-to-end, it helps save a considerable amount of time and expedite the entire onboarding process (which further improves the new joiner’s experience).
2. Access Creep
During mid-lifecycle transitions, users often retain access to their previous permissions even after being assigned new ones. So over time, they accumulate excessive privileges (commonly referred to as access creep), creating security loopholes.
Just imagine, if such an account is ever compromised, attackers can exploit the accumulated access to infiltrate multiple apps, potentially causing more damage than normal.
How does IGA address it?
Identity governance solutions mitigate this issue by allowing your team to configure automated mover workflows. They simply need to define the transition –
- Who is moving to which role/department/designation
- Which permissions should be revoked, and which new ones should be granted
Once the conditions are met, the platform automatically removes outdated access and provisions the necessary new access. This helps ensure that users are not left with any lingering permissions.
3. Creation Of Orphaned Accounts
In many organizations, offboarding processes are still handled manually.
- HR first checks who is offboarding
- Then sends an email to notify IT.
But at times, HR forgets to send the email altogether.
Adding to the challenge, IT teams manually offboard users one at a time, which introduces further delays.
As a result –
User accounts tend to remain active even after the employee departs, which leads to the creation of orphaned accounts. And, these accounts serve as entry points that attackers can exploit to gain unauthorized access to systems.
How does IGA address it?
- Identity governance solution helps prevent this by automatically notifying IT via Slack and email when an employee is marked for departure – no human intervention is needed.
- It then allows your IT to trigger an automated offboarding workflow that promptly deactivates the account and revokes access across all systems – all at once.
List Of Common Problems Organizations Face During Access Request Management & How an Identity Governance Platform Helps Address Them
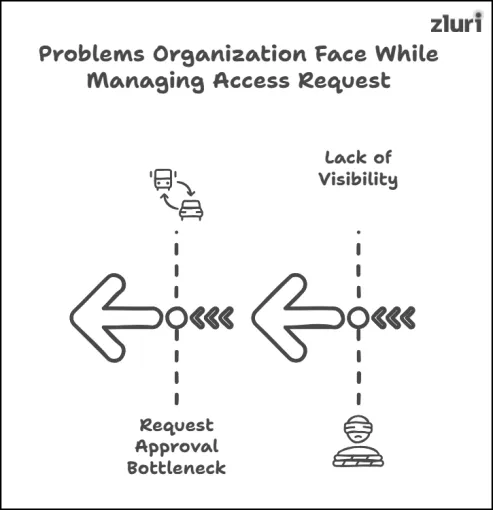
1. Lack Of Visibility Into Incoming Access Requests
In most organizations, IT teams ( or whoever is assigned the tasks of approving requests) often rely on manual ticketing systems, where –
- Users submit requests via email
- IT teams (or approvers) manage approvals manually
The problem with this approach is –
- Emails pile up in the IT team’s inbox
- Critical requests get lost among other access requests
What’s worse is that the absence of a centralized view of all incoming app access requests makes it even more difficult for IT teams to track and prioritize them efficiently.
As a result, critical requests often go unnoticed and remain unaddressed/unresolved for an extended period.
How does IGA address it?
Identity governance solutions address this issue by bringing all incoming access request data into a single, centralized dashboard. Along with that, it provides important insights like –
- Who submitted the access request?
- When it was submitted,
- Which app access is being requested?
- The reason behind the access request (why),
- The status of each request (whether it's pending or completed).
With the help of this visibility, IT teams can easily prioritize which requests need to be addressed first, and no access requests will be left unaddressed.
2. Request Approval Bottleneck
IT teams are often required to manually approve every incoming access request – whether critical or non-critical.
For each request –
- IT first needs to assess who submitted it, what access is being requested, and whether it aligns with the user’s role and responsibilities.
- Then decide whether to approve or deny the request. And they have to repeat the entire process for every subsequent request.
This, in turn, consumes a significant amount of time and effort.
How does IGA address it?
Identity governance solution eliminates these hassles by allowing your team to configure an auto-approval workflow for non-critical access requests.
They simply need to specify under what condition an access request can be approved. Once those conditions are met, the system automatically approves the requests.
This saves plenty of time and improves user experience by eliminating the waiting period (they no longer have to wait to get their access requests approved).
Also Read: Importance Of Automating Access Requests
A Common Problem Organizations Face During Access Certification & How Identity Governance Platform Helps Address Them
1. Overshoots Review Deadlines
According to Zluri’s State of Access Review report, 77% of organizations still manually perform access reviews.
- IT teams first reach out to department heads or application owners to gather user access data. Then, they compiled the data into spreadsheets and shared it with reviewers,
- After that, the reviewers further analyze the data to determine whether access should be revoked or modified.
Once decisions are made, reviewers notify IT to remediate the access anomalies detected during the review.
- The IT team then logs into each application individually to update or remove access permissions.
- At last, they compile a review report manually.
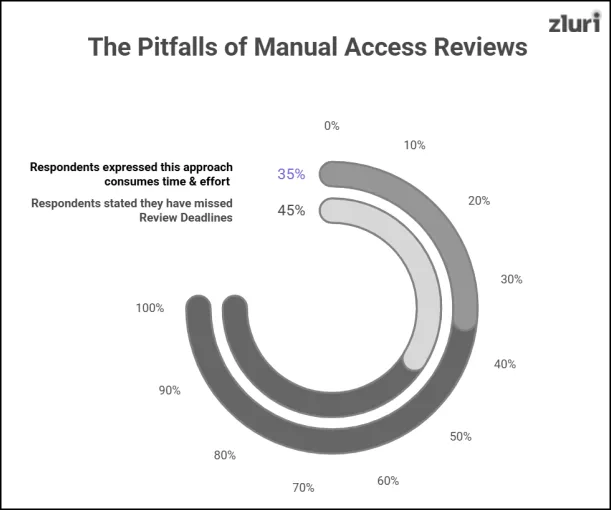
This entire process consumes a lot of time and effort (even in Zluri’s report, 35% of respondents have expressed the same). As a result, review deadlines are often missed (as per Zluri’s report, 45% of respondents confessed the same), which ultimately compromises compliance efforts.
How does IGA address it?
Identity governance solutions address this problem by automating the access review process.
- It integrates directly with applications.
- Provides reviewers with all the necessary context to make informed access review decisions quickly (whether to allow the user to continue to retain access, modify the access, or revoke it).
- It allows IT teams to trigger automated deprovisioning and access modification workflows to remediate the access misconfiguration.
- At last, it auto-generates audit-ready review reports. Post-access review
This reduces manual effort, improves accuracy, and ensures reviews are completed on time, which also further helps successfully achieve compliance certification.
SaaS Management Platform: A Solution Designed To Provide Visibility Into What Applications Are In Use
A SaaS management platform is a purpose-built solution that helps manage and optimize SaaS applications by providing complete visibility into SaaS app licenses, application usage, and SaaS spend.
What problems does it help resolve?
It addresses two main problems:
- Shadow IT
- Spiking SaaS expenses
It typically helps tackle every portal issue that one can face while managing a SaaS stack.
List Of Common Problems Organizations Face While Managing SaaS & How a SaaS Management Platform Helps Address Them
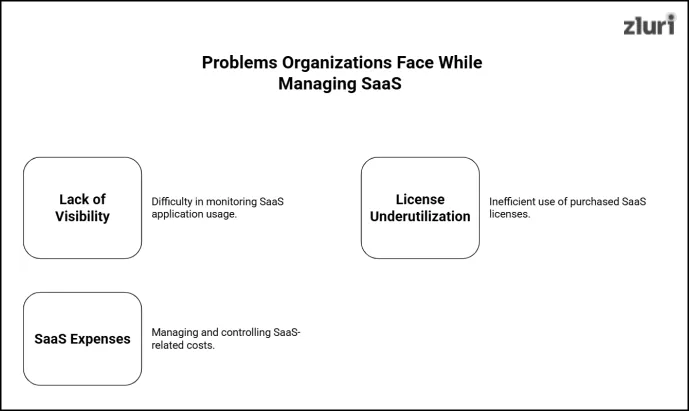
1. Lack Of Visibility Into SaaS Applications
According to Josys' SaaS management report, 85% of organizations still don’t have complete visibility into their SaaS applications.
This blind spot isn’t surprising because with the surge in the adoption of SaaS and the rapid shift towards a cloud-based environment, every organization has flooded its tech stack with SaaS apps.
- With such a sprawling ecosystem, it's easy to lose track of which apps are being adopted.
- Also, due to a decentralized setup, employees are getting the freedom to procure and use SaaS apps without seeking IT’s approval, which is contributing to the rise of shadow IT.
How does a SaaS management platform help address it?
SMP uses different discovery methods to automatically uncover which SaaS apps exist in your SaaS stack, including those not approved by the IT teams, also known as shadow IT.
Further, with this visibility, it becomes easier for the IT team to effectively manage, organize, and secure the organization’s SaaS apps.
2. SaaS License Underutilization
According to Zylo, on average, organizations now use 275 SaaS apps, but shockingly, 53% of licenses go unused within 30 days.
Why are they facing this issue?
Because they do not have proper visibility into license usage. Their team cannot tell –
- Who is actively using the app
- Who hasn’t used the app in the past 30 days
- Which licenses are not yet assigned
- Which licenses are still assigned to users who have already left the company
This happens because they rely on spreadsheets to monitor license distribution and usage – an approach that is outdated and inefficient. As a result, they struggle to optimize the licenses.
How does Sa aaS management platform help address it?
SMP helps solve this issue by providing your IT teams with a central dashboard that shows each SaaS license usage information in a detailed manner –
- Which licenses are assigned
- Who is using them
- Which ones are going unused, and more
With this information, your teams can reassign unused licenses to users who need them or reduce the number of licenses they purchase during the next renewal.
This way, you can ensure that every license is utilized to its fullest potential.
3. SaaS Expenses
According to Zylo, organizations in 2025 are losing an average of $18 million annually on unused SaaS licenses. What’s driving this massive waste?
- One main reason is purchasing more SaaS licenses than required (as they don’t have visibility into the license usage) to simply address ‘just in case’ needs.
- Many organizations don't have the tools to identify which applications are unused.
- Another major culprit is auto-renewals. Even for apps no longer in use, licenses continue to renew quietly in the background, draining budgets without adding value.
How does a SaaS management platform help address it?
SMP provides a comprehensive SaaS optimization summary that highlights unused licenses and under-provisioned licenses (where reallocation is possible).
With the help of these insights, you can cut down on unnecessary spending, reassign idle applications, and get value for every dollar you have invested in the SaaS license.
After going through the comparison, you might have understood what each solution is meant for. So, now let’s understand their correlation.
Co-Relation Between Identity Governance And SaaS Management Platform
Even though identity governance and SaaS management platforms are designed to tackle different sets of challenges, they function/operate best when they work together.
- For example, SaaS management platforms provide complete visibility into who has access to what applications and usage patterns.
Identity governance solutions can then use these insights to carry out access certification (validate whether a user should have access to that app or not) and handle role transitions (revoking app access that the user previously held and giving them new app access).
- Similarly, identity governance solutions provide insights about which identities have been given access to which apps and whose app access has been revoked.
The SaaS management platform then uses these insights to identify which SaaS licenses are actively in use and which are unused and can be reassigned.
Now, you’ll probably ask – ‘Does this mean we have to purchase two separate solutions to get better results?’
- You can have a disparate setup, where you can purchase two best-of-breed SMP and IGA solutions to serve the purpose.
But the problem with this setup is that you might struggle to integrate them because not every third-party solution can connect with other SaaS solutions.
- Instead of having a disparate setup, you can go for a converged solution. Converged solutions are unified platforms that offer both IGA and SMP capabilities under one roof. No hassle of integration!
But which converged solution to opt for?
There are several options available; however, the one that truly delivers results is Zluri.
Zluri offers next-gen IGA and SMP solutions (it’s a unified fabric setup; both solutions are pre-integrated so that they can work seamlessly with each other).
They are designed to deliver 360-degree visibility into –
- SaaS stack
- Application usage
- License
- Licence spend,
As well as automate –
- JML cycle
- Access approval
- Access review
(Note: To learn more about Zluri, you can book a demo)









.svg)



























.webp)







.webp)
.webp)





.webp)