Is there a way to ensure your organization meets ISO 27001 requirements? Yes. The ISO 27001 Statement of Applicability (SoA) allows you to map the applicable controls to your organization's specific needs. This post will discuss its importance and steps to create a successful SoA.
According to Statista, global business risks due to cyber incidents will be the highest in 2024. Cyber crimes, IT failures or outages, data breaches, and others are all included in these incidents. These could bring your operations to a standstill, damage your organization's reputation, and incur hefty penalty fees.
As a result, attaining ISO 27001 certification is a remedy for securing your organization. It demonstrates your pledge to information security to the various stakeholders, thus gaining their confidence.
However, ISO 27001 certification is not just a matter of policy deployment; it also focuses on accomplishing the target. To do so, you need an ISO 27001 Statement of Applicability (SoA). An SoA is a document that specifies the controls that your organization opts to have and the justification for opting them.
Now, let's explore the ISO 27001 Statement of Applicability in detail.
Importance of ISO 27001 Statement of Applicability (SoA)

Let’s discuss the importance of the ISO 27001 Statement of Applicability.
- Simplifies the process for auditors: The SoA will give the auditors a clear view of your selected security controls and why you chose or excluded certain controls. Moreover, it helps the auditors to evaluate your ISMS efficiently.
- Provides a quick overview of ISMS: The SoA, a central document, helps you organize all your relevant information in a single place. This gives you easy access to details about your ISMS, saving time and effort.
- Acts as a guide for internal and certification audits: Your SoA will help your team prepare for assessments by ensuring that all controls are implemented correctly. The SoA shows your compliance with ISO 27001 requirements for certification audits, ensuring a smooth audit process.
6 Steps to Create an ISO 27001 Statement of Applicability

To create an ISO 27001 statement of applicability (SoA), follow the steps below.
1. Understand your ISO 27001 requirements and the controls
The first step in creating an ISO 27001 statement of applicability is to have a detailed understanding of your ISO 27001 requirements and controls.
The SoA, an important document in your ISMS, shows which controls are applied, why they are chosen, and how they meet your organization’s security needs. Understanding them in detail will help you choose the appropriate controls that align with your organization’s security needs.
For example, Annex A of the ISO 27001 standard consists of 93 controls, each addressing different security risks. Studying these in detail will help you identify risks relevant to your organization and take action accordingly.
Moreover, understanding these controls clarifies how to safeguard your data and allows you to explain your security measures to auditors and stakeholders.
Also Read: Know more about ISO 27001 Requirements.
2. Conduct a thorough risk assessment
The next step in creating the ISO 27001 statement of applicability is to conduct an in-depth risk assessment. This process will help you identify and analyze risks to your ISMS, ensuring your SoA becomes a strategic step in assessing your organization’s risk.
Imagine your organization might face risks like inefficient access controls. Without assessing them, your ISMS might lack the ability to protect your organization’s critical information. However, by performing a risk assessment, you will identify risks that will show you where your assets are most vulnerable.
Moreover, you can analyze those identified risks to prioritize which areas need the most attention. This makes your security efforts efficient and effective. It will also ensure that you focus on what matters instead of implementing generic controls.
3. Define your risk treatment plan
This step of creating an ISO 27001 statement of applicability outlines how your organization will address the risks you have identified. Not all risks are the same. Some require immediate action, while others may need ongoing monitoring. Without a treatment plan, it’s easy to overlook critical risks or waste resources on low-priority ones.
Thus, defining your risk treatment plan will help you prioritize your actions. Moreover, your risk treatment plan directly informs the controls included in your SoA. It identifies which ISO 27001 Annex A controls are necessary to mitigate specific risks, ensuring the alignment of the SoA with your organization’s needs.
In addition, a clear risk treatment plan helps to explain the reason behind your decisions. For example, you can document why certain risks are accepted or why specific controls are implemented. This transparency will strengthen the credibility of your SoA.
Note: When defining your plan, you can choose from four risk treatment options:
- Avoid the Risk: Change or stop activities that create the risk.
- Reduce the Risk: Implement controls to lower the likelihood or impact of the risk.
- Transfer the Risk: Shift the risk to a third party, such as through insurance or outsourcing.
- Accept the Risk: Acknowledge the risk and decide it’s within acceptable limits.
Each option should be chosen based on the nature of the risk and its impact on your organization.
4. Choose the applicable security controls to mitigate your risks
Choosing the right security controls is crucial for effectively addressing the identified risks. This step of the ISO 27001 statement of applicability will prevent unnecessary control implementation, which might lead to resource waste without adding value.
Moreover, your selected controls form the backbone of your ISO 27001 SoA. This will document how you address risks and demonstrate your commitment to ISO 27001 compliance. A well-thought-out selection of controls ensures your SoA is a clear and actionable document.
For example, if your risk assessment highlights the risk of unauthorized access to sensitive data, you might choose access control measures like multi-factor authentication (MFA) or user access reviews. Documenting these choices in the SoA shows how you are mitigating this specific risk.
5. Prepare your SoA document
Now comes the most important step: to prepare your ISO 27001 statement of applicability (SoA) document. This mandatory document will list the controls you have selected, explain why they have been applied, and state how they are helping you to address your organization’s risks.
For example, if you implement encryption to secure sensitive data, the SoA explains why encryption is needed and how it mitigates a specific risk.
This document serves as a roadmap for your ISMS. It helps you stay organized, providing which controls are in place and why. This makes it easier to review, update, and communicate your security measures as your organization grows.
Here are a few tips you should follow before preparing your SoA document.
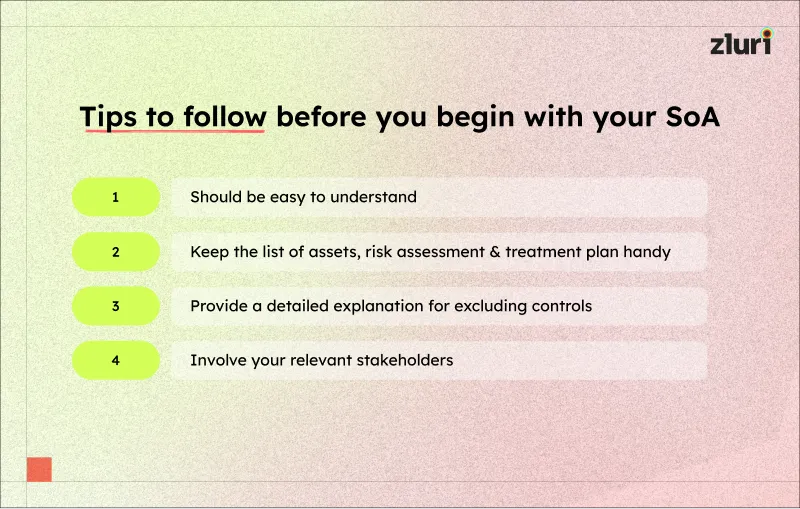
6. Keep your SoA updated
It is important to keep your ISO 27001 statement of applicability updated. An updated SoA helps you show that your security measures are aligned with current threats and your organization’s needs. It also projects your commitment to compliance with the ISO 27001 standard.
During the audit process, auditors look for evidence that your information security management system (ISMS) is progressing with your organization. An outdated SOA can lead to non-compliance and impact your organization’s reputation. Thus, updating your SOA will ensure that you are ready to address risks as they arise.
Now, the question arises: how do you keep your SoA updated?
- You can conduct regular, quarterly, or bi-annual reviews of your SoA. During these reviews, check whether the listed controls are relevant and effective.
- Monitor organizational changes that could impact SoA. For example, new technology, processes, or partners may introduce new risks.
- Leverage tools to track the changes in your ISMS. Some platforms can notify you when updates are needed, making the process smoother and more accurate.
Click here to download the ISO 27001 Statement of Applicability template.
What Should an ISO 27001 Statement of Applicability Include?
Let’s discuss the important things to include in your ISO 27001 Statement of Applicability.
- The SoA should include a list of the Annex A controls. These controls cover various security domains, such as access control, incident management, and cryptography. Each control must be evaluated to determine whether it applies to your organization’s needs.
- The SoA must state whether every control is implemented or not. This transparency will help during audits, ensuring that security measures are clearly defined.
- If a control is excluded, a strong justification must be provided. This explanation shows that the decision is based on thoughtful risk assessment and not oversight.
- The document should also briefly describe how each applicable control is implemented. This summary will highlight the steps taken to enforce the control and demonstrate its relevance.
- Additionally, the SoA should reference the policies or detailed procedures that explain the control in greater depth. This ensures auditors and stakeholders can track each control and its implementation.
Which Version of ISO 27001 Statement of Applicability is Required?
If your organization is seeking certification, you must align with the latest version of ISO 27001. The most recent version, ISO/IEC 27001:2022, includes updated controls from Annex A and decreased the number of controls from 114 to 93. Also, the 14 categories in the previous version have been updated to only four categories – organizational, people, physical, and technological.
Therefore, using the updated version of the SoA ensures you account for all necessary controls. Further, your organization can effectively meet audit expectations and protect critical information assets with the updated version.
Stay ISO 27001 Compliant by Creating a Strong SoA
Staying ISO 27001 compliant requires more than creating an SoA for your organization. It also requires ensuring that your organization's security measures are relevant. Creating a strong SoA will guide your team to align policies, processes, and controls with ISO standards.
To build a strong ISO 27001 statement of applicability, you need accurate data on access rights, user activities, and system vulnerabilities. This is where Zluri's access review solution can make a difference. Zluri simplifies the process of reviewing access permissions across your organization. It provides clear insights into who has access to what and ensures all permissions comply with security policies.
Moreover, by leveraging Zluri, you can conduct regular access reviews and remove excessive privileges. This reduces the risk of breaches and strengthens your compliance efforts. With Zluri, staying ISO 27001 compliant becomes a manageable, streamlined process.
Note: Invest in the right compliance automation platforms today to stay compliant with the regulatory standards.
Also Read: Want to stay compliant with ISO 27001? Consider reading the ISO 27001 checklist.
Frequently Asked Questions (FAQs)
1. What is ISO 27001 SoA?
The Statement of Applicability is a key document for ISO 27001 certification. It lists the Annex A controls your organization has chosen to address information security risks and those you've decided to exclude. This document is usually kept for internal audits and shared only with your team and the certification body.
2. What is the ISO 27001 certification process?
The ISO 27001 certification process includes:
- A gap analysis is needed to identify areas needing improvement
- Implement an Information Security Management System (ISMS) and relevant controls from Annex A
- An internal audit ensures everything is in place before a certification body conducts an external audit
- If all requirements are met, the organization receives the certification
- Regular audits are done afterward to maintain compliance
3. What is the sequence of ISMS implementation?
The sequence of ISMS implementation involves:
- Define the scope of your ISMS
- Create a clear Information Security Policy
- Establish a risk assessment methodology
- Conduct risk assessments and implement treatments
4. What is the statement of the applicability list of the ISO 27001?
The Statement of Applicability (SoA) outlines your organization's information security controls, which are taken from ISO 27001 Annex A, also known as ISO 27002.
5. What is a risk assessment report?
A risk assessment report is a critical document that outlines the findings of a security control assessment. It focuses on identifying risks to a system and its environment and their potential impact on the organization.






.svg)


























.webp)







.webp)
.webp)





.webp)