Within the identity governance domain, you’ll find three primary IGA players: legacy, modern and next-gen. Each has been developed for a specific environment and to address different challenges. Which one is right? In this article, we’ll discuss the key difference between the three to help you decide.
Aren’t all identity governance and administration solutions designed to serve the same core purpose (i.e., ensuring only the right user gets the right app access)?
Technically yes. But, the methodologies, technologies, and features they use to achieve the goal varies.
In fact, the environments they operate in are also quite different.
For instance –
- Legacy IGA solutions are built for static (where number of identities and apps are fixed and don’t fluctuate) and on-premises environment.
- Meanwhile, modern and next-gen IGA solutions are purpose-built for today’s dynamic (where users, devices, cloud apps, and access points change constantly) environment and hybrid infrastructures (blend of on-premise and cloud setup).
This is just a glimpse of how they are different. You cannot solely consider this factor to make decision.
To truly find the right fit for, you need to dig deeper and understand
- What each type of IGA solution brings to the table
- Where they fall short
So, let’s dive into the differences of legacy vs modern vs next-gen IGA.
Legacy IGA: A Solution That Is No Longer Suitable For Cloud-First World
According to Omada’s State of Governance 2025 report – nearly 40% of organizations (i.e., 4 in 10 organizations) still rely on legacy IGA solutions.
It’s a first-generation IGA solution that is installed, run, and maintained within organization’s own physical servers, instead of being hosted in the cloud.
Note that – legacy IGA solutions can be:
- Either internally developed by the company (home-grown)
- Or else can be a commercial product (offered by IGA service providers such as SailPoint Legacy IGA)
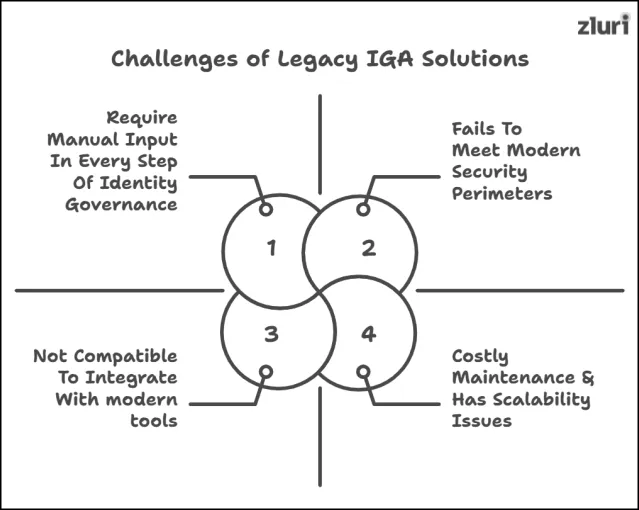
1. Integration Complexities
Legacy IGA solutions often rely on proprietary technologies, i.e., closed-off technology built and controlled exclusively by the organization or service provider, and the underlying source code is kept private. Due to this closed setup –
- They are not compatible to integrate with newer, modern tools and platforms.
- Lack of compatibility further causes – silos, different apps and systems end up operating in isolation which scatters critical data across multiple platforms.
As a result, obtaining accurate and complete information regarding identity and their access becomes very difficult.
- If you want to integrate them with a modern set of tools, it typically demands complex coding – a task that cannot be handled by non-technical users.
As a result, it takes a long time to realize value (long implementation process, longer time-to-value).
2. Require Manual Input In Every Step Of Identity Governance
Legacy IGA systems were not built with automation in mind. Nearly every step involved in identity governance and administration requires manual intervention.
- Data Collection
- IT teams chase department heads and app owners for identity and access data
- Joiner Mover Leaver management
- New hires: IT manually creates accounts across systems
- Role transitions: IT revokes old permissions and grants new ones manually
- Access Reviews
- Reviewers sift through spreadsheets to validate user access
- IT manually remediation of anomalies discovered during reviews
The Consequences? Slows down the identity governance and management process, increases the risk of human error, overshoots audit deadlines, and more.
3. Costly & High Maintenance
Since these solutions are hosted on-premises, organizations have to invest a lot in –
- Physical data centers
- Servers
- Backup systems
- IT service centers
- Networking equipment
These assets not only come with hefty upfront costs but also require regular patching and updates (adding up to extra expenses).
On top of that, they depreciate over time and eventually organizations have to replace them.
Also, since legacy IGA uses proprietary technology, organizations have no choice but to invest in training their in-house development and IT teams to configure the solution or outsource experts.
Either way, it’s going to cost quite a bit.
This fact is even stated in Omada’s State of Governance 2025 report, 60% of the respondents stated that the total cost of ownership (ToC) for maintaining a legacy IGA system is quite high.
4. Scalability Issues
Legacy IGA systems are built for static, predefined environments – where the number of identities and connected resources are limited and stable (the numbers don't fluctuate much).
However, today’s modern workplaces are anything but static; they are dynamic and evolving rapidly. Organization have hybrid or remote setups, adopting new SaaS apps constantly and continuously expanding their workforce – and these outdated IGA solutions just aren’t built to handle such worksetup.
Simply put, legacy IGA are not designed to accommodate this kind of growth. It often requires complicated changes that can be expensive to implement and maintain.
5. Fails To Meet Modern Security Perimeters
Legacy IGA solutions struggle to meet the norms of new modern security perimeters. Why? Because they are designed to follow a reactive approach, instead of a proactive one.
- These outdated solutions respond and address security incidents only after they have occurred – such as investigating a breach post-incident, detecting policy violations after the fact, or revoking access only once it's been misused.
Result?
This will leave organization’s identities and sensitive data vulnerable to serious security risks.
Meanwhile, modern security perimeter requires organizations to follow a proactive approach. This approach involves continuous monitoring, real-time risk detection, and predictive analytics to prevent security incidents from happening in the first place.
Why Not Just Reconfigure Legacy IGA?
- Most legacy IGA source code is restricted or too complex to modify
- Even if possible, changes require:
- Significant development effort
- Risk of downtime
- Potential breakage of existing functionalities
Bottom line: Even if you adopt proactive practices, you won’t be able to fully implement them – because legacy systems won’t have the built-in capabilities required to support the approach.
Modern IGA: A Solution Designed To Fix What Legacy Identity Governance Couldn't
According to Zilla’s 2025 State Of IGA Survey report, only a small percentage (6% approx) of organizations have deployed fully automated modern IGA solutions.
Modern IGA solution is an updated version of legacy IGA tool designed to meet the needs of today’s dynamic, cloud-first, and hybrid IT environments.
They are cloud-native, meaning they are hosted, operated, and updated entirely in the cloud. Since these solutions are run on-cloud, it brings forth multiple benefits.
Note that – modern IGA solutions can be internally developed. However, out of the 6% that use modern IGA, about 84% prefer vendor-provided best-of-breed modern IGA solutions, rather than building them internally.
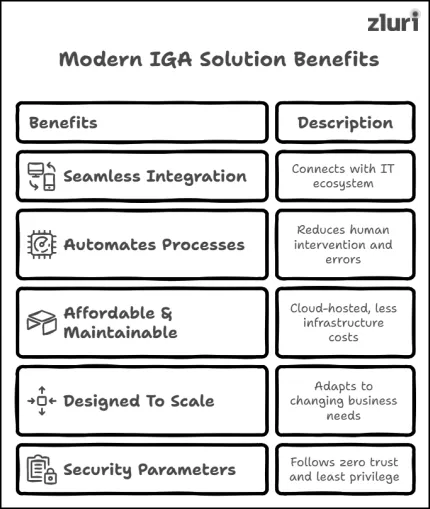
1. Supports Seamless Integration
Modern IGA solutions leverage a diverse set of integration technologies to seamlessly connect with your existing IT ecosystem.
- They utilize REST APIs to integrate with modern cloud and web-based applications, and SOAP APIs to integrate with traditional enterprise-grade systems such as Oracle and SAP.
- To connect with directory services like Active Directory (AD), they leverage LDAP. Also, at times they use webhooks as well as iPaaS platforms for integration purposes.
This means, you no longer have to worry about your apps and systems operating in silos, as modern IGA solutions make sure every app and system — be it, cloud-based or on-premises — is fully connected.
Result?
- This integration setup eliminates data fragmentation, allowing SaaS app and identity-related information to flow consistently and securely across all platforms.
Plus, they offer pre-built connectors that allow you to directly integrate with commonly used applications. This in turn, speeds up the implementation process and reduces the time-to-value.
2. Automates End-To-End Processes
Modern IGA solutions eliminate the need for constant human intervention by automatically handling most of the routine identity and their access management tasks.
This includes –
- Creating identity’s account,
- Granting them access,
- Modifying their access during mid-lifcycle transitions,
- Revoking access upon identity’s departure
- Collecting access data from connected apps in real-time for access review purposes
Result?
- Less mistakes (as there will be minimal human involvement),
- Eases administrative burden,
- Speeds up the process no more overshooting audit deadlines or keeping users waiting for access)
In fact, according to Zluri’s State of Access Review report –
‘Organizations that have opted for automated modern IGA are able to reduce their error rates by 40% on average. In fact, they are also able to cut down the time spent on tasks like access reviews by 40% (taking just 4 days to complete a review cycle).’
3. Affordable & Easy To Maintain
Since modern IGA solutions are hosted on cloud,
- You don’t have to bear the cost of setting up a physical infrastructure, such as –
- Building server rooms or data centres,
- Purchasing networking equipment (e.g., routers),
- Installing security systems (e.g., surveillance cameras), and more.
- Instead, you simply need to pay a license subscription which is comparatively more affordable than establishing an entire ecosystem to support an IGA solution.
- You don’t have to worry about updating the solution (overall maintenance), everything is taken care of by the modern IGA solution’s service providers.
- No need to invest in specialized training for your team or hire external experts to operate the platform because these solutions are user friendly, even non-technical users can use them. No more extra expenses piling up!
- Can even cut down on labor costs, as you won’t need a large team to run modern IGA and manage the entire IGA process – just a few hands can get the job done.
In fact, it’s even stated in the Zluri’s State of Access Review report that organizations that used modern IGA have reduced the number of employees managing the access review process by 30%, on average.
4. Designed To Scale
Modern IGA solutions are dynamic by nature – built to adapt to today’s fast-changing business environment.
No matter if you are expanding your workforce, introducing new SaaS apps, or handling hybrid or remote teams, these modern solutions scale effectively to meet your needs.
Simply put, these solutions can accommodate your evolving needs, that too without any complicated reconfigurations or expensive upgrades.
5. Adheres To Modern Security Parameters
Modern IGA solutions follow a proactive approach – i.e., the requirement of modern security standards.
- They follow the zero trust security model, no identity (be it external or internal users) or service account is trusted by default; every access request is verified before it’s granted.
- They also adhere to the principle of least privilege, ensuring that users are only given the least necessary level of access permissions required for their role or to perform certain tasks – nothing more, nothing less.
- To prevent accumulation of lingering or unnecessary access (which can create access gaps in the long run), they allow you to perform micro access certification on a regular basis and clean up the access anomalies.
Together, these practices –
- Lowers the probability of organization’s data being exposed to cyber threats,
- Help satisfy the security obligations (such as., maintaining confidentiality, integrity, and availability of data CIA triad) set forth by compliance regulations.
However, modern IGA solutions do have a few limitations such as:
Limitations Of Modern IGA Solutions
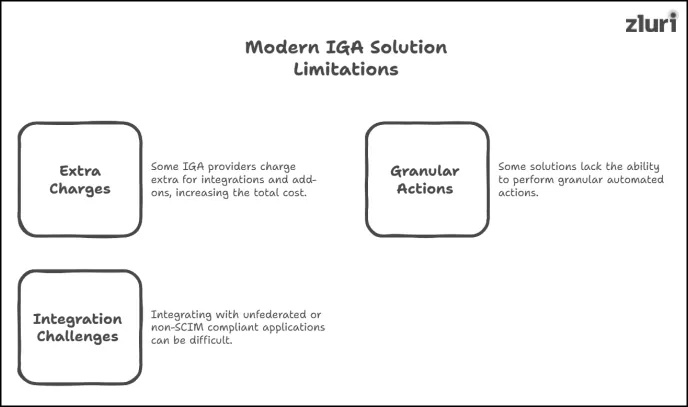
1. Charges Extra Costs For Integrations And Add-On Features/Modules
While many modern IGA providers offer all-inclusive pricing, some of them like –
- Okta’s IGA charges extra for third-party application integrations and add-on modules (like adaptive SSO & MFA).
- Saviynt’s IGA also charges additional costs for advanced features and add-on modules.
These extra charges can add up quickly, making the total cost of ownership (ToC) higher than expected.
2. Cannot Perform Granular-level Automated Actions
Most modern IGA solutions outperforms legacy IGA by automating most IGA tasks, but some of them lack the ability to perform granular automated actions like –
- Running workflows based on conditional logic,
- Setting variable-based triggers,
- Or customize approval paths.
For example–
- Modern IGA solutions like SecureEnd cannot perform closed-loop remediation post access review.
- Omada cannot trigger workflows based on conditions or policies.
- AccessOwl cannot run slack-centric workflows.
3. Integration Challenges Beyond Federated and SCIM-Based Applications
Modern IGA solutions like Lumos often struggle to integrate with unfederated, non-SCIM compliant, or generative AI-based applications.
These types of apps generally fall outside the standard integration frameworks, making it difficult for some modern IGA tools to connect with them seamlessly.
As a result, organizations may face challenges in gaining complete visibility into user identities and their access data.
Next-Gen IGA: The Upgraded Version Of Modern IGA
Next-gen IGA solutions are basically the upgraded version of modern IGA. They have set the benchmark for what identity governance and administration solutions should deliver today and beyond.
It offers all the benefits that modern IGA solutions offer be it –
- Eliminating silos by seamlessly integrating applications and systems,
- Automating end-to-end identity governance and access management process,
- Aligning with new security norms,
- Delivering affordability and scalability.
Along with that, they address the critical limitations that modern IGA solutions have yet to overcome.
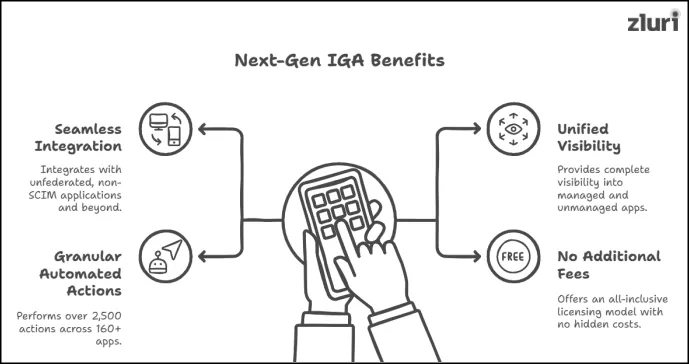
1. Seamlessly Integrates With Unfederated, Non-SCIM Applications & Beyond
Next-gen IGA solutions like Zluri leverages it native iPaaS engine to integrate with any type of application within minutes (not months), including the ones that are traditionally hard to connect, such as:
- Unfederated apps (apps not connected to a IdPs)
- Non-SCIM apps (apps that don’t follow the SCIM protocol for identity data sharing)
- Legacy or on-premise systems
- Gen AI-based apps
- Apps with no public APIs
In fact, Zluri offers 300+ out-of-the-box connectors which allows you to directly integrate with commonly used applications such as HRMS and fin apps – no-coding required.
Also, it offers custom builder SDKs (kind of a developers tool kit), that developers can use to create custom code or script to create connection between Zluri and those hard-to-integrate apps (like apps that don’t have public APIs).
2. Provides Unified Visibility
Zluri leverages its patented discovery engine to provide you complete visibility into –
- Managed and unmanaged apps,
- Shadow IT,
- What identities are accessing and their attribute details.
- Activity trends over 30/60/90 days,
- First and last used timestamps,
- Dormant entitlements,
- Over-provisioned access,
- Contextual risk insights.
What’s even better is, it compiles all these data and presents them in a centralized easy-to access dashboard.
Your team/admins can further use this data to perform different sets of actions such as provisioning, access adjustment, deprovisioning, access reviewing, and SaaS management.
Basically, Zluri acts as a single source of truth – providing accurate, complete, and up-to-date data that your team can rely on to make informed decisions during identity governance and access management processes.
3. Has The Ability To Perform Granular Automated Actions
Next-gen IGA Zluri allows you to perform over 2,500+ actions across 160+ apps.
- In-App Actions
With Zluri, you can perform granular in-app actions within both onboarding and offboarding workflows. For example, within Zluri’s onboarding workflow, you add a user to different Slack channels, and define what exact permissions should the user hold in Okta.
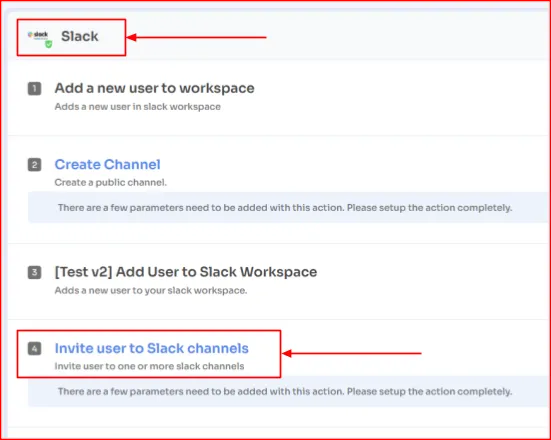
Meanwhile, within the offboarding workflow, you can transfer data ownership to admins or other users, reassign application license, and more.
- Conditional Actions
With Zluri, you can create conditional playbooks. You just need to define the conditions, and based on those conditions, ‘the playbook and the workflow actions that you have specified within it’ will run automatically.
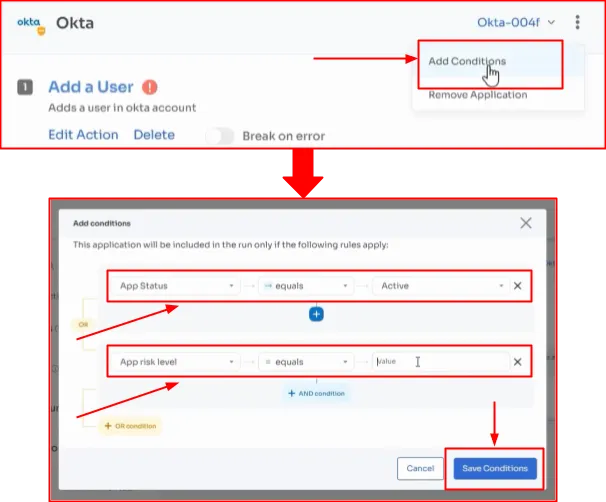
- Automation Rule/Policy Engine
With Zluri, you get the flexibility to define your own granular automation rules.
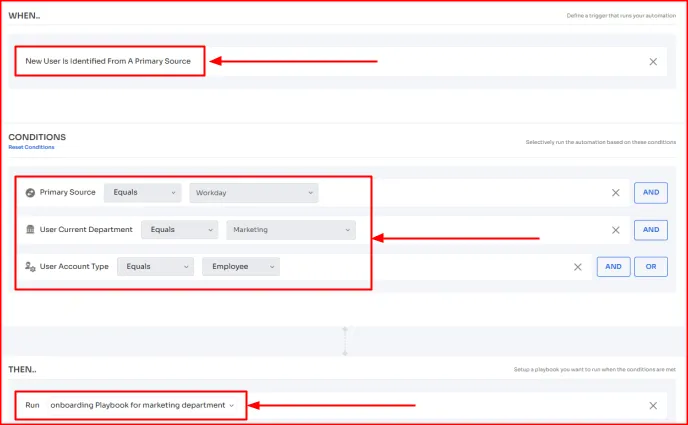
For example, you want to create a rule stating – whenever a new employee from the marketing department is detected in Workday (primary source), they should be given access to all the marketing tools.
So for that, you can outline the following details in the automation rule workflow:
Once triggered and conditions are satisfied, Zluri will automatically grant the marketing department employees access to the specified tools (the ones that are specified in the marketing department playbook). No need to create a separate workflow for each new hire!
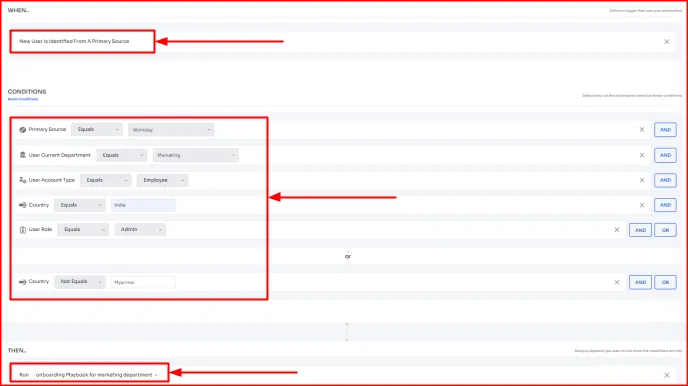
What’s even better is that – you can even use Zluri’s automation rule workflow to enforce access controls, like –
- Role-based access control (e.g., only marketing admins get tool access and no one else)
- Contextual-based access control (e.g., grant the admins access, only if they are based in India, or do not give access to it if they’re from restricted regions like Myanmar).
Once the rules/controls are configured, Zluri will automatically apply them across whenever it detects a match (when the conditions are met by a user) in your user base.
- Workflow Variables
With the help of Zluri, you can add and use various workflow variables to make your automation more precise and dynamic.
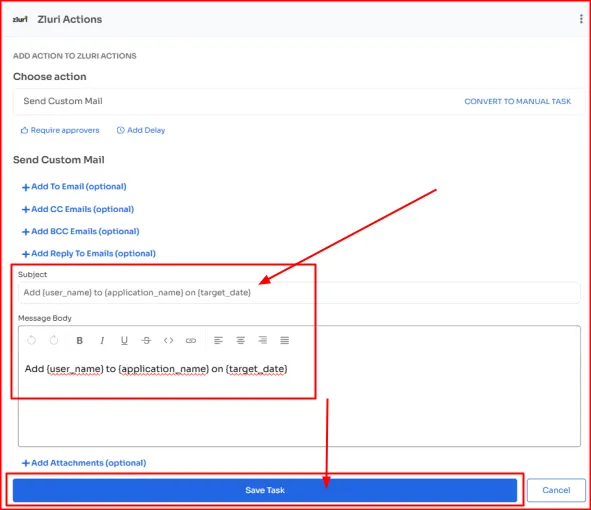
Suppose, you want to send an email to the all finance app owners, requesting them to grant ABC user access to the app by the end of the week.
In such a case, you can use the variables in the workflow; simply specify details like –
- The user’s name
- The application name,
- The target date into the email template and click on add the action.
Once the playbook is published, the finance app owners will get notified automatically. No need to send emails individually.
4. Doesn’t Charge Additional Fee For Integration & Add-Modules
Next-gen IGA, like Zluri, offers an all-inclusive licensing model, meaning everything you need is included in one pricing package. Unlike modern IGA solutions that charge extra for each integration or add-on module, Zluri provides all the necessary capabilities without charging any extra. Basically, no hidden costs or surprise fees are there.
Legacy IGA Solution Era Is Over – Embrace What’s Next In Identity Governance & Administration
Let’s face it – legacy IGA solutions simply cannot keep up with today’s dynamic, evolving IT environment. Why? Because security attacks are becoming more sophisticated and compliance regulations are getting more stringent day by day, relying on outdated IGA systems will simply put your organization at risk.
So what you need to do is rethink your approach – don’t cling to legacy IGA – modernize it.
But here’s the thing – if you’re ready to modernize, don’t stop halfway.
Instead of settling for just a basic upgrade, why not choose an next-gen IGA solution that is built for the future? Next-gen IGA doesn’t just help you catch up; it helps you leap ahead.









.svg)



























.webp)







.webp)
.webp)





.webp)