Still relying on legacy on-prem IGA to manage a hybrid workforce, expanding SaaS stack, and modern security threats? It's time to modernize before your IGA becomes your biggest vulnerability.
According to Omada’s State of Governance 2025 report, nearly 40% of organizations still haven’t deployed cloud-based (SaaS) IGA solutions.
What’s holding them back?
- For many, it's the fear of disruption: downtime, integration challenges, and unexpected costs. Others stick with the mindset: "If it isn't broken, why fix it?".
But that hesitation comes at a price. Legacy on-prem IGA systems might have served their purpose in the past, but today they hinder your progress. They limit scalability, increase maintenance overhead, and introduce security blind spots.
In a cloud-first world, where agility is critical, doing nothing (as in, not upgrading) is no longer a neutral decision; it’s a risky choice. Standing still while everything around you evolves is how organizations fall behind.
Still wondering what exactly makes legacy IGA so problematic today? Let’s find out.
Key Limitations of Legacy On-Prem IGA
Customer Testimony – “Legacy IGAs are originally built for an on-prem environment, and only later have they been retrofitted to work in the cloud. However, the cloud capabilities they offer are very basic.
A legacy IGA solution is typically installed and managed on an organization's own physical or virtual servers, rather than being delivered as a cloud-based service.
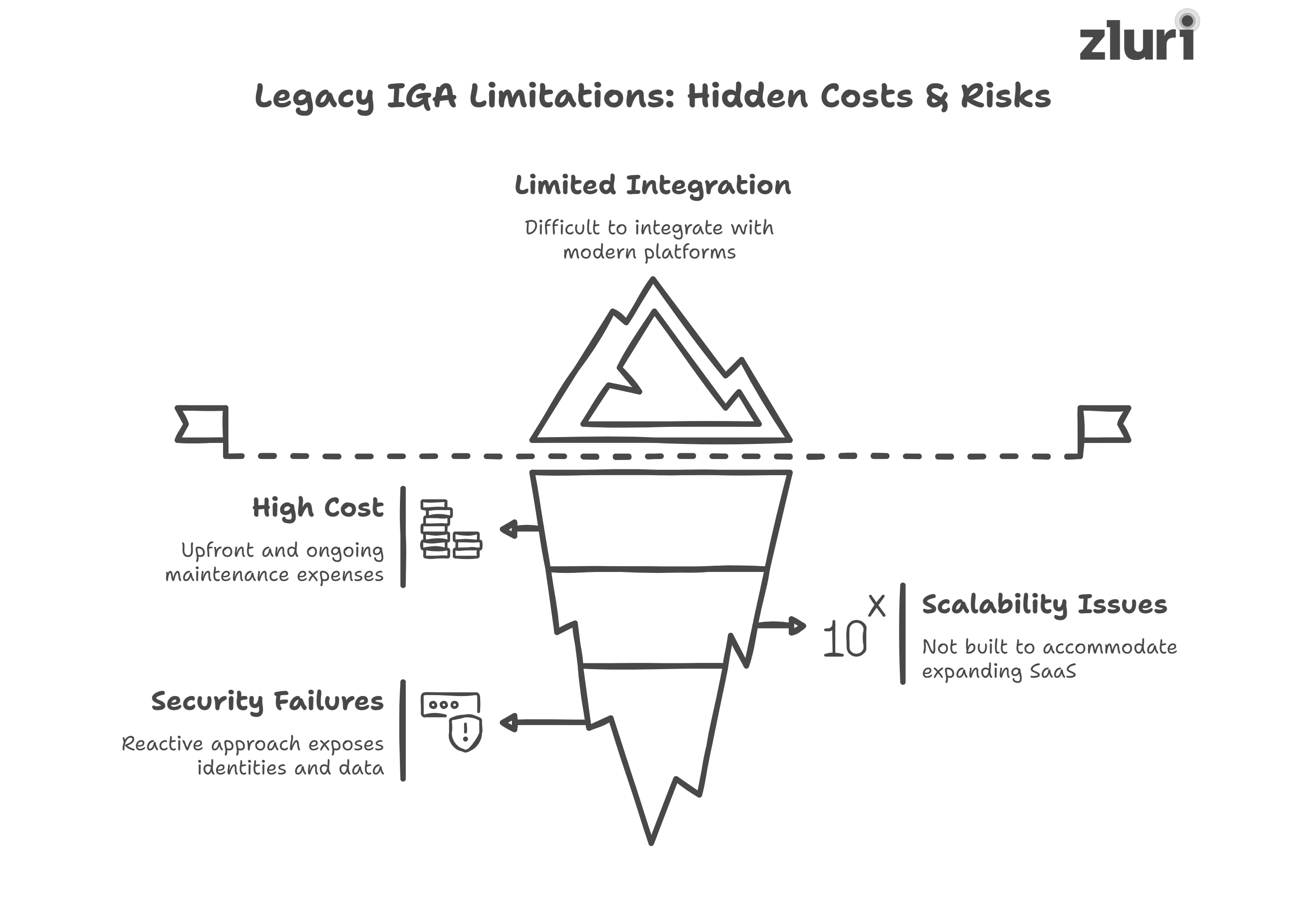
- Limited Integration
- Legacy on-prem IGA uses proprietary technologies, which make it difficult to integrate with newer, modern platforms.
- If you want to connect these legacy systems with a modern set of tools, it usually requires complex coding – a task that non-technical users cannot handle.
Customer Testimony
“It takes years to fully implement legacy IGA. A company with 500 employees can expect to spend anywhere between $300k to $500k on the implementation process.”
- High Cost & Operational Overhead
- You need to bear the upfront and ongoing maintenance expense of
Servers, networking gear, backups, and data centers. - To operate the legacy IGA, you need to have a team of experts, so you must either train your existing team or hire an external consultant.
- Scalability Issues
Legacy on-prem IGA systems are designed to operate within static, predefined environments. They are not built to accommodate an expanding SaaS stack or rotating. It often requires complicated changes that can be expensive to implement and maintain.
- Fails To Meet Modern Security Perimeters
Legacy on-prem IGA solutions fail to adhere to new modern security perimeters because they follow a reactive approach, instead of a proactive one. This means –
- Respond only after incidents occur: Instead of preventing breaches, they act post-damage.
- Leave identities and data exposed: Vulnerabilities remain until detected too late.
Now, the question is – ‘how to overcome these challenges?’ By modernizing your legacy on-prem IGA.
But how is modernizing legacy on-prem IGA going to help? Read on to find out.
How Modern IGA Solves Legacy Challenges?
Modernizing your legacy on-prem IGA doesn't just remove bottlenecks of older systems; it unlocks automation, scalability, and better security.
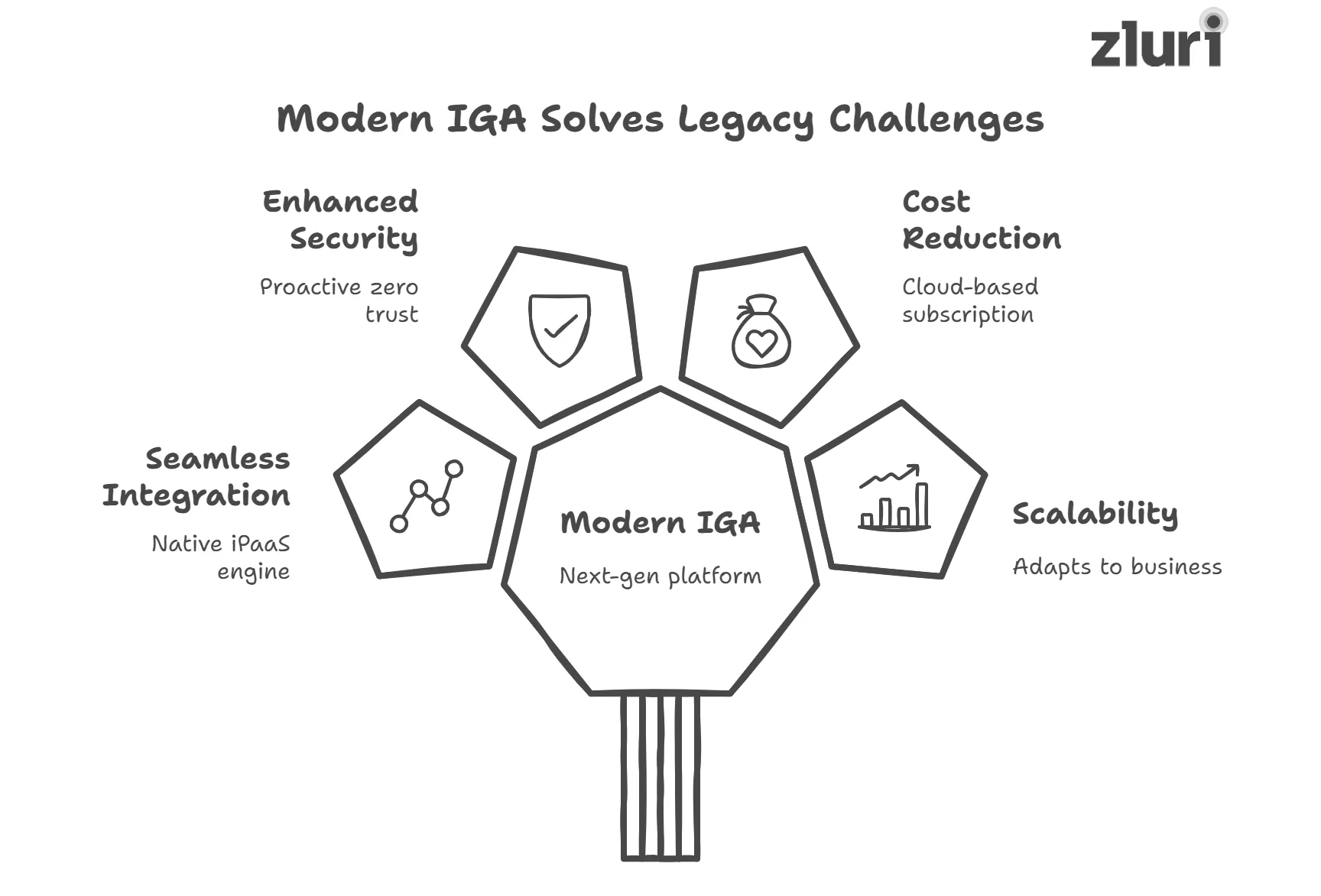
Below, we'll show how a next-gen platform like Zluri helps you overcome the exact limitations we explored earlier.
1. Seamless Integration
.webp)
Modern IGA solutions like Zluri leverage a native iPaaS engine to seamlessly integrate with –
- Your existing SaaS apps,
- Third-party apps,
- Custom tools,
- Even on-premise infrastructure.
No matter if it's IdPs, HRMS, developer tools, SCIM apps, non-SCIM apps, or any other apps present in your tech stack.
Customer Testimony – "Zluri integrates with your existing systems like your identity provider (IdP), HRMS, and SaaS applications and uses the fetched identity and app data to trigger automated workflows and enforce access governance rules."
Other benefits –
- It offers over 300 prebuilt integrations (connectors) with popular SaaS and cloud apps, which means you can easily connect these apps to Zluri without writing any code.
- If an app doesn’t have a standard API, Zluri lets you create your own custom integration using scripting tools provided in its Software Development Kit (SDK).
- Unlike legacy on-prem IGA systems that take weeks or even months to integrate, Zluri completes the process in just a matter of minutes.
- It fetches accurate and up-to-date data that you can further use to govern your identities and their access.
2. Meets Modern Security Parameters
Unlike legacy IGA, which relies on a reactive approach, Zluri follows a proactive approach – i.e., meeting modern security standards.
.webp)
- Zluri thoroughly follows the zero trust security model, which means it always verifies identities and service accounts before granting access – no access is given by default.
- It adheres to the principle of least privilege, ensuring that users receive only the least necessary level of access permissions required to perform their tasks – no more, no less.
- It allows your team to perform micro access certification (validating identity access permissions) regularly.
Result?
- Reduce the chances of the organization’s data being exposed to cyber threats.
- Help satisfy the security obligations (such as maintaining confidentiality, integrity, and availability of data, CIA triad) set forth by compliance regulations.
Customer Testimony – “As our company grew, employees kept accumulating access they no longer needed, creating unnecessary risk. IGA helped us regain control and reduce that access sprawl.”
3. Comparatively Less Costlier
Zluri are comparatively cost-effective. Here’s why:
.webp)
- Since it is hosted in the cloud, you don’t have to purchase and maintain expensive physical servers or infrastructure.
- It follows a subscription-based license model, making it easier for you to predict your expenses and allocate your budget effectively.
- You don’t need to hire specialized IT professionals or consultants to install, manage, and troubleshoot the software. With basic training, your existing team can manage it easily.
- It doesn’t charge additional fees for integrations, helping you further cut down your expenses.
4. Built To Scale With Your Organization
.webp)
Zluri is dynamic by nature – designed to adapt to today’s evolving business environment.
Whether you are expanding your workforce or introducing new SaaS apps to your stack, Zluri scales effectively to meet your needs – that too without any complex reconfigurations or costly upgrades.
Legacy On-Prem vs Modern Cloud-Based IGA: Comparison Table
However, it’s important to understand that you cannot just directly switch. To successfully modernize your legacy on-prem IGA, you need to consider several factors and follow a structured series of steps.
4 Steps To Modernize Your Legacy On-Prem IGA
Below, we’ve listed the steps that you can follow to modernize your legacy on-prem IGA.
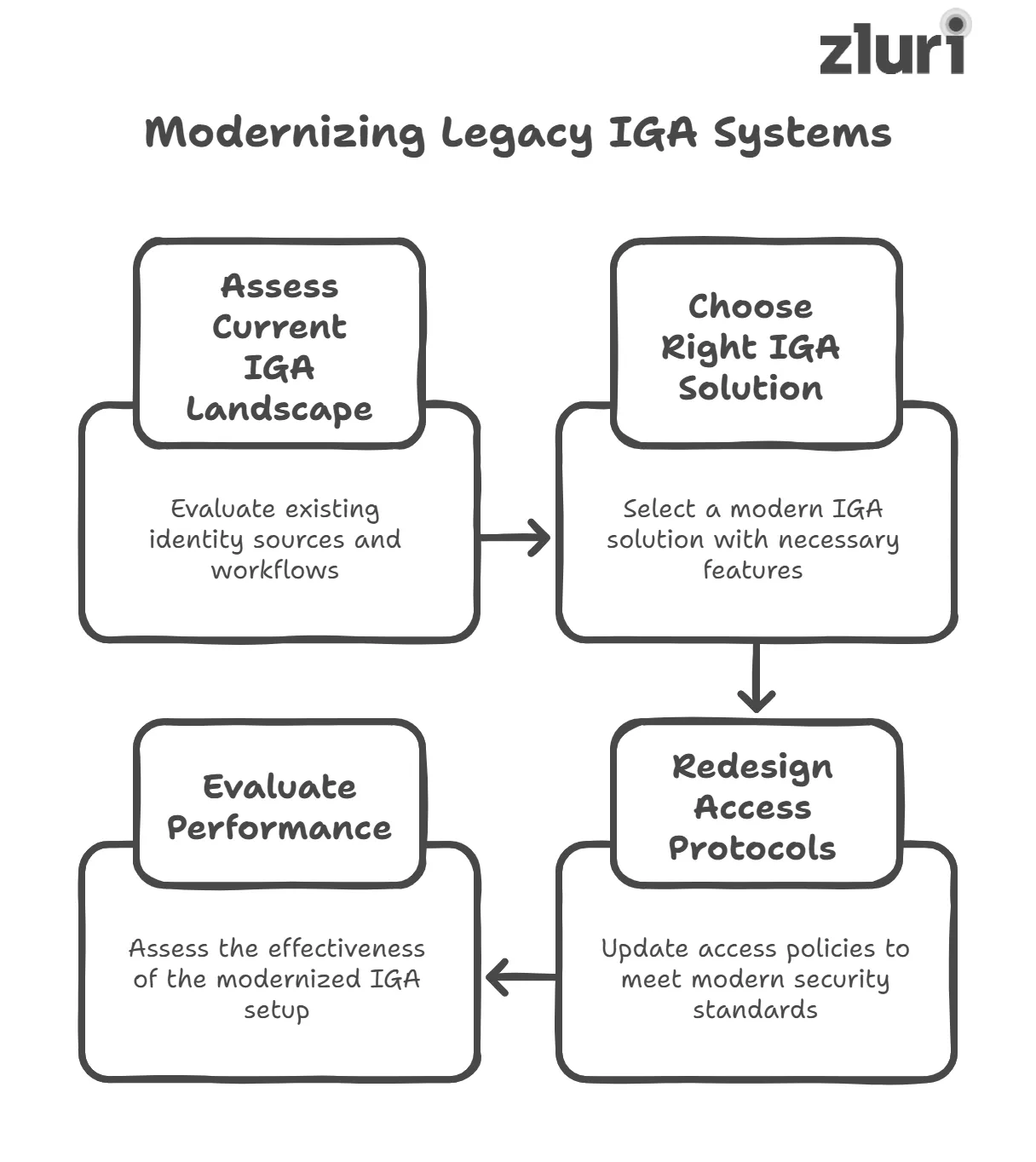
Step 1: Assess Your Current IGA Landscape
Start by mapping your identity sources: Active Directory and HRMS, and other systems storing user and access data. Knowing where identities live will help you prevent gaps or data loss during migration.
.webp)
Next, evaluate how your current IGA workflows perform:
- How quickly are users provisioned or deprovisioned?
- What's the average access request resolution time?
- How long do certification cycles take?
Also, assess how much manual intervention is involved in day-to-day operations. This will help you identify automation opportunities.
Finally, review your existing access policies. What's working well? What isn't? This will help you know what to keep and what to improve during the transition.
Step 2: Choose The Right IGA Solution
Choose a modern IGA solution that addresses the weaknesses of your current setup. Prioritize platforms that offer:
.webp)
- A wide range of out-of-the-box connectors and supports seamless integration with multiple applications.
- No-code or low-code configuration options to reduce complexity and speed up deployment.
- License pricing that aligns with your budget.
- Strong automation across provisioning, certification, and access reviews.
Customer Testimony: “It is better to have a modern IGA that sends an alert when users switch roles, so access can be updated in real-time.”
Step 3: Redesign Access Protocols For Modern Security Standards
.webp)
Your legacy access policies aren't meant for the zero trust world. Once your modern IGA is deployed, establish new protocols that align with today's security and compliance standards.
Incorporate the zero trust model, the principle of least privilege, segregation of duties, and other access controls in your policy.
This way, you will be able to meet the modern security parameters, updated compliance regulations, and address sophisticated threats.
Step 4: Evaluate The Performance Of Modernized Setup
.webp)
After deploying the IGA solution and enforcing new access policies, you need to evaluate how they are performing. How to do that? Check the following –
- Is the modern IGA solution able to resolve the inefficiencies you faced with your legacy setup?
- Are identity workflows more streamlined?
- Has manual effort decreased?
- Also, check if your updated access policies are helping you meet current security standards/laws and comply with relevant regulatory requirements.
Note: This evaluation is best done after 6 months of deployment or post your first official compliance audit (which is after completion of one year).
Jump On The Trend & Unlock The Potential Of Modern IGA
By modernizing your IGA, you step into the future of governance, gaining more control over every access activity within your IT environment. Plus, you cut down the chances of encountering any security or compliance issues.
The point is, legacy IGA can’t keep up with today’s dynamic environments, so make the switch before you fall behind competitors – or worse, end up in the next headlines for a security breach.









.svg)



























.webp)







.webp)
.webp)





.webp)