If your organization stores, processes, or transmits cardholder data (whether credit card details or transaction history), adhering to PCI DSS compliance is mandatory. Failing to meet it can have serious consequences, including lawsuits, fines, and loss of customer trust. Therefore, you need to find ways that can help successfully meet PCI DSS, and that’s exactly where ‘PCI DSS user access review’ comes in.
As you may already be familiar with, to achieve PCI DSS compliance, you must meet multiple mandatory requirements (e.g., PCI DSS requirements 1, 2, 7.3, 8, and 10) – as listed by the PCI DSS Council.
Now, that might sound overwhelming, but the good news is – by performing one strategic practice, i.e., “PCI DSS user access review (UAR)”, you can contribute to fulfilling certain other PCI DSS requirements.
You’ll probably have a couple of questions now, such as – ‘Which requirements does UAR help fulfill? How exactly do they help achieve them?’
To provide you with complete clarity, we’ve outlined below the key PCI DSS requirements that PCI DSS user access review helps address, along with a clear explanation of how it does so.
Note: PCI DSS user access review helps specifically fulfill the sub-requirements of PCI DSS requirement 7, which states, “Restrict access to system components and cardholder data by business need to know.”
Key PCI DSS Requirements That User Access Reviews Helps Meet
Below, we’ve explained in detail how PCI DSS user access reviews help meet PCI DSS requirements.
.png)
1. PCI DSS Policy & Procedure Management Requirement 7.1.1
Now, how will performing PCI DSS user access review contribute to meeting this requirement? Here’s how.
By performing a PCI DSS user access review, you can verify whether the implemented policies and access control procedures are functioning as intended.
- How? During the PCI DSS user access review, if the reviewer detects a large volume of access discrepancies, be it unauthorized users holding access to apps (that hold cardholder data) or unnecessary excessive privileges granted to non-admins.
- Then, this depicts the policies that you’ve implemented, and the enforcement mechanisms are simply not working; improvements are needed. Meanwhile, if minor access discrepancies are identified, no improvements are required. Simply remediate them; that's it!
The cause of these access discrepancies can be:
- Outdated Policies: Perhaps your policies haven’t been updated. Your team may have added new systems or apps, but failed to include them in the existing policies and access control procedures.
As a result, these apps are left uncovered by policy, allowing users to gain access without proper authorization.
- Poor Communication: Alternatively, the policies may exist but haven’t been properly communicated to department heads, line managers, or team leads. And if they don’t know the rules, you can’t expect them to enforce them correctly.
Now, this can lead to granting unnecessary access to users or allowing them to retain excessive permissions.
In short, after conducting PCI DSS user access review, you will gain insight into whether there are any issues with your policies and procedures. If issues are detected, you can make further efforts to resolve them, and once they are fixed, you will be able to meet the PCI DSS requirement 7.1.1. Simple!
2. PCI DSS Access Approval Requirement 7.2.3
.png)
Simply put, to meet PCI DSS requirement 7.2.3, you’ve to ensure that the assigned authorized personnel (be it – IT admin, department head, or app owner) formally approve user(s) to gain and retain access privileges (admin permissions).
Now, how does PCI DSS user access review play a role in fulfilling this requirement?
Even though your team may have carefully checked and approved users’ privilege requests during role transition, there is still a chance of mistakes. They might unintentionally approve access requests for users who shouldn’t hold those privileges (although it may not happen often, the possibility is always there).
This is where the PCI DSS user access review comes into play. By conducting a PCI DSS user access review, you have the opportunity to double-check whether the user(s) truly need the access privileges they hold (i.e., whether the specified privileges match the roles assigned to the individual).
- During the PCI DSS user access review, reviewers (other personnel, not those previously involved in approving the access) can take a fresh look at the situation.
- They can take different considerations into account, such as whether a user's role actually needs those access privileges, or if similar roles (peers) are holding the same set of access privileges. They can also verify the user's ID (a unique identifier).
Based on the evaluation, they can easily determine whether to approve a user's access permissions (as in allowing them to continue with the access rights they hold).
Essentially, by incorporating the practice of performing PCI DSS user access reviews, you can establish a double-approval setup. Initially, access privilege requests will be verified and approved by the appointed approvers. After that, the reviewers can step in and cross-evaluate and approve those access privileges.
This will help ensure that no user without legitimate requirements will hold access privileges.
3. PCI DSS Periodic Review Requirement 7.2.4
Now, by performing PCI DSS user access reviews regularly (at least once every 6 months), you can directly meet PCI DSS requirement 7.2.4.
However, note that you also need to review access permissions of:
- Third-party vendor
- Accounts used to access cloud services (e.g., AWS, Google Cloud)
- Seasonal workers/freelancers
When reviewing their access, if any inappropriate access is detected, ensure it is remediated promptly, with the same urgency and precision as you would apply to remediate internal users' inappropriate access.
4. PCI DSS Application & System Account Management Requirement 7.2.5
PCI DSS requirement 7.2.5 states, “all application and system accounts and related access privileges are assigned and managed as follows:
- Based on the least privileges necessary for the operability of the system or application.
- Access is limited to the systems, applications, or processes that specifically require their use.
Simply put, to fulfill PCI DSS requirement 7.2.5, you have to ensure application & system accounts (which are non-human/service accounts) hold the least level of necessary access privileges to perform operations/specified tasks without any interruption.
Now, how does PCI DSS user access review help fulfill this requirement?
By performing PCI DSS user access review, you can validate whether the access permissions assigned to these accounts align with their intended scope of work.
.png)
- Basically, during PCI DSS user access review, reviewers can analyze which systems or applications these accounts interact with, especially those that store, process, or transmit CHD.
- Additionally, they can assess whether the permissions they hold within those applications are suitable or not.
- If any misalignment is detected, you can immediately rectify it (for example, by revoking or modifying their permission) and safeguard CHD from unauthorized access.
Now the real question is – ‘how to perform PCI DSS user access review?’ There are two main methods: the ‘application-based approach’ and the ‘user-based approach’. What do these approaches exactly mean? Below, we’ve provided a clear explanation of both approaches.
.png)
- Application-Based Approach: This user access review method involves reviewing the access permissions of all users who have access to a specific application. Essentially, reviewers select an application and review the access permissions of all users who have access to it.
- User-Based Approach: This user access review method involves reviewing all the applications to which a particular user has access. Typically, reviewers select a user, then assess the applications to which they have access and the level of permissions they hold within those applications.
Which Approach Is More Effective For Achieving PCI DSS Compliance?
Based on our experience, we recommend adopting an application-based approach when working toward achieving PCI DSS compliance (or any other type of compliance, for that matter).
Why, you may ask. The reason is simple: PCI DSS primarily focuses on protecting cardholder data.
Therefore, you only need to review the applications that store or process sensitive cardholder information. Applications that do not handle cardholder data can be reviewed later, either after the formal PCI DSS audit is complete or at any time thereafter.
We don’t recommend using a user-based approach in this scenario, as it will simply consume your team's productive time.
How? Reviewers first need to identify which applications each user has access to and then sort the relevant apps for review. Further, this practice will divert your reviewers' focus away from the critical applications that truly matter for PCI DSS compliance.
Now, you might be wondering – ‘which solution follows the user-based review approach?’ Well, there are several IGA solutions that follow this approach; however, one that stands out for its intelligent features is Zluri. What does it offer? How does it work? Let’s find out.
Leverage Zluri To Perform PCI DSS User Access Review
Zluri offers an advanced ‘access review’ solution that enables your team to set up and configure certification campaigns, automating the end-to-end PCI DSS user access review process. Here’s how it works:
Note: Below, we’ve properly explained how Zluri helps in every stage of the PCI DSS user access review process
Stage 1: Data Collection
With Zluri, your team no longer has to chase down department heads or app owners for user data, and you won't get involved in spreadsheet chaos.
All they have to do is specify the application (in this case, select an app that holds CHD) in the access certification workflow, and Zluri takes care of the rest. It first integrates with the app and then auto-fetches accurate, up-to-date, and complete user information such as
- Who’s using it
- What is their role
- Which department do they belong to
- What is user employment status
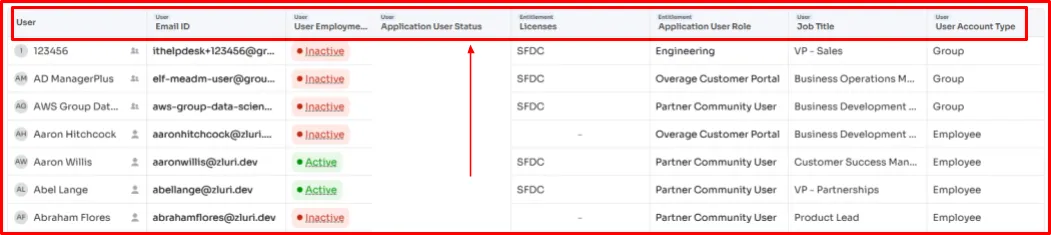
And every other crucial detail needed for access review. The best part is that it consolidates all that information, organizes it, and presents it in a centralized dashboard, making it easier for reviewers to examine the user data.
Stage 2: Review
The task of reviewing access is inherently a judgment-based process and cannot be automated. However, that doesn’t mean reviewers have to rely on their gut feeling or surface-level knowledge about the user. Instead, they can leverage Zluri.
Zluri equips reviewers with contextual risk insights that go beyond surface-level data, such as orphaned accounts, privileged users, inactive users (those who haven’t interacted with the app in the past 30 days), external users, and more.
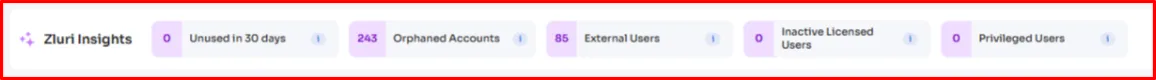
With the help of these insights, reviewers can make smarter, more informed decisions (which access certification action to take – approve, revoke, or modify access permissions).
Bonus Feature: Access Review Delegation
- To prevent conflicts of interest and maintain the integrity of the access review process, Zluri provides reviewers with the option to delegate their reviewing tasks.
In scenarios where a reviewer has access to the applications themselves, Zluri allows them to delegate the review task to another authorized individual. This ensures they are not put in a position where they’re reviewing their own access (preventing conflict of interest).
Here, the delegated reviewer acts as a neutral party, bringing an impartial perspective to the reviewing process. This further helps ensure that access decisions and review outcomes are free from bias.
- Additionally, this feature is particularly helpful when reviewers encounter access held by higher-level users—such as executives or system administrators—whom they are not authorized to review. In such cases, they can delegate the task to someone with the appropriate authority.
To gain more clarity check out this blog - Access Review Delegation: A Quick Guide
Stage 3: Remediation
Typically, reviewers have to submit individual tickets for each access misalignment they detect (i.e., creating an email for every discrepancy, outlining the reason, and sending it to the IT team). However, this approach is not only time-consuming, but it also carries a high risk of tickets getting lost in the process.
To address this issue, Zluri takes a more effective approach.
It allows reviewers to simply select the access certification action and submit a comment – a single click action.
Note: They can even perform bulk actions (like revoke all the inactive users' app access).
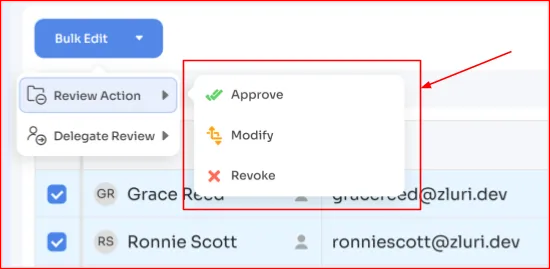
Once submitted, Zluri immediately notifies the IT team via email or Slack, ensuring that no access misalignment slips through the cracks. From there, your IT team can take over and perform the remediation action.
What’s even better is that Zluri makes this remediation process easier for the IT team as well. It allows IT teams to pre-configure deprovisioning and downgrade licensing playbooks that, once triggered, automatically perform the necessary remediation actions (i.e., removing access and adjusting licenses).
Stage 4: Reporting
Zluri records every detail during the access review process, so that no important information is missed. After the review, it auto-generates a user access review report (UAR) that outlines the reviewer, the access evaluated, the decisions made (approve, revoke, or delegate), and includes comments explaining the rationale behind the decisions.
This UAR not only provides transparency but also gives audit teams exactly what they need—clear, organized, and ready-to-share evidence of a well-executed review.
(Check out the Zluri access review tour for more clarity – Azure AD access review.)
Zluri doesn’t stop at simplifying PCI DSS user access reviews for achieving PCI DSS compliance – it goes above and beyond. It further helps meet other PCI DSS sub-requirements 7. Here’s how it does that:
Also Read: PCI DSS v4.0: Exploring What's New in the Latest Version









.svg)



























.webp)







.webp)
.webp)





.webp)