Insider threats can compromise sensitive data, disrupt operations, and damage your organization's reputation. How do you stay ahead of the curve and protect your organization? In this article, we explore the top five best practices for insider threat detection that you should know to enhance a security-first culture in your organization.
What if the biggest threat to your organization's security is not from outside attackers but from within your team? Insider threats are becoming a growing concern for businesses. Cybersecurity Insiders (2024) reported that 48% of organizations have seen an increase in insider attacks over the past year.
But, insider threats are not necessarily driven by malicious intentions. Often, employees are unaware that they are exposing sensitive data or disrupting operations. If those you trust most become your biggest risk, how do you protect your systems?
Traditional security tools primarily focus on external threats and often overlook insider activities. One misstep can lead to a serious incident, including unauthorized access, accidental sharing of confidential information, data breaches, operational downtime, and damage to your organization's reputation. Can your current security measures detect and prevent these threats in a timely manner?
Detecting insider threats requires organizations to adopt proactive best practices. Techniques involved in it include developing top-notch tools that monitor user behavior, identify any unusual patterns, and send alerts at the right moment when a risk arises.
In this article, we will discuss some of the best practices for insider threat detection, as well as provide other valuable information to protect your organization. To begin, let's break down the types of insider threats and the various indicators associated with them.
Types of Insider Threats
Here, we will explore the various types of insider threats.
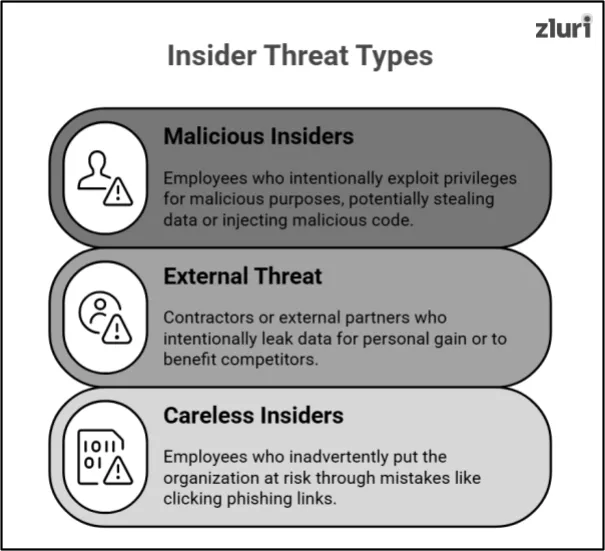
1. Malicious Insiders
Malicious insiders are employees, contractors, or partners with authorized access who intentionally exploit their privileges for malicious purposes. In the SaaS industry, they might:
- Steal customer data or intellectual property to sell to competitors.
- Inject malicious code into applications, causing service disruption.
- Sabotage cloud infrastructure to damage operations or demand ransom.
Such threats can lead to data breaches, loss of customer trust, and regulatory penalties under compliance standards such as SOC 2, GDPR, and HIPAA —all critical in SaaS operations.
2. External or Third-Party Threat
External or third-party threats may include contractors or even external partners. Their actions are often intentional, meaning they are intended to leak valuable data for personal gain or to benefit competitors. In the SaaS industry, they might:
- Sell confidential information to competitors or use it to harm your reputation.
- Manipulate systems, sabotage workflows, or introduce vulnerabilities.
Such threats lead to data leakage, and consequently, to fines and litigations under regulatory law. The loss can be huge as a result of stolen trade secrets or lost customers. External threats may even damage your reputation by eroding the trust of customers and other stakeholders.
3. Careless Insiders
Careless insiders are employees or contractors who inadvertently put your organization at risk. They are not malicious but careless or ignorant. Their mistakes may result in the leakage of sensitive data or create vulnerabilities. In the SaaS industry, they may:
- Click on phishing links, which can lead to data breaches.
- Share login credentials or use weak passwords.
- Accidentally misconfigure systems or store sensitive data in unsecured locations.
A single mistake can lead to a data breach, affecting your organization’s reputation. Cybercriminals might exploit vulnerabilities created by these errors. Furthermore, your organization may suffer financial losses due to compliance violations.
Insider Threat Indicators: 5 Warning Signs to Know
Here are five key indicators of insider threats.
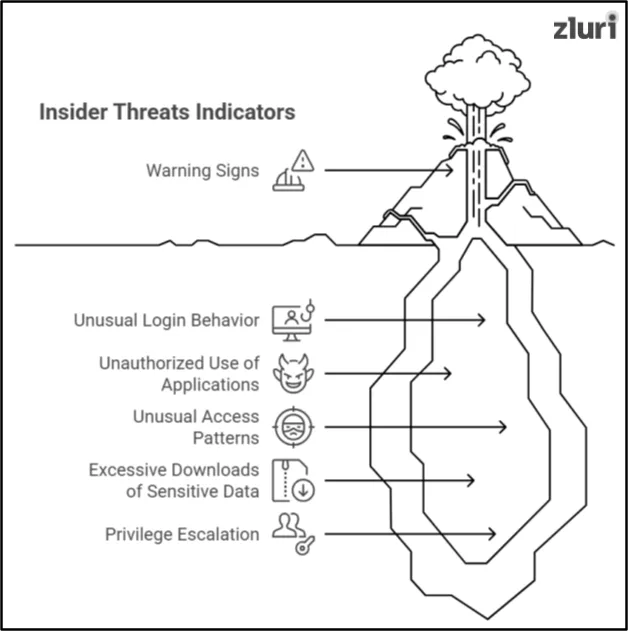
1. Unusual Login Behavior
One major red flag is unusual login activity. This includes logging in from unfamiliar locations, devices, or at odd hours. Repeated failed login attempts can also signal a potential issue. Such behavior might indicate a compromised account or an insider misusing credentials.
2. Unauthorized Use of Applications
Insiders using applications they are not authorized to access is another key indicator. For instance, an employee accessing financial systems without permission could signal malicious intent. Unauthorized use often bypasses security controls, increasing the risk of data exposure.
3. Unusual Access Patterns
Unusual access to files or systems that are unrelated to an insider's role can also indicate a threat. This might involve accessing large volumes of data or sensitive directories. Such actions could be a precursor to data theft or sabotage.
4. Excessive Downloads
An insider downloading excessive files or sensitive data is a critical indicator. This behavior is often linked to data exfiltration. The insider might intend to misuse the information or share it with external parties.
5. Privilege Escalation
Privilege escalation occurs when an insider gains access to higher levels of authority than they are authorized to have. For example, a regular employee accessing admin privileges is a clear warning sign. This often points to an insider seeking sensitive data or systems to exploit.
Best Practices for Insider Threat Detection
Let’s discuss the best practices for effective insider threat detection.

1. Identify the compromised accounts in your organization
Compromised accounts pose a significant risk to an organization's security. These accounts belong to legitimate users but are compromised by attackers who have stolen their credentials. Identifying these accounts is a crucial step in detecting insider threats. It helps you prevent unauthorized access and minimize potential damage.
This best practice focuses on monitoring user behavior for unusual activity. For example, if an account accesses sensitive files it typically doesn’t use or logs in from an unexpected location, it could indicate a compromise. Tools equipped with user behavior analytics (UBA) make this process more efficient by flagging suspicious patterns in real-time.
By identifying compromised accounts early, organizations can prevent potential threats from escalating. This holistic approach helps reduce the risk of data breaches, fraud, and operational downtime. It also supports compliance with security standards by ensuring proper account monitoring.
2. Conduct sentiment analysis to uncover insider threats
Sentiment analysis is a new and effective practice for insider threat detection. It uses advanced technology to evaluate text for emotional tones. Analyzing emails, chat messages, or other text-based interactions can reveal negative sentiments such as anger, frustration, or dissatisfaction. These emotions often signal potential risks.
For example, a disgruntled employee may exhibit negative sentiment before engaging in harmful actions, such as data theft or sabotage.
Moreover, with real-time insights, sentiment analysis allows you to detect unusual behavior patterns early. This gives your team a chance to intervene and prevent possible damage. It also helps to create a culture of awareness and accountability within your organization.
3. Monitor your third-party access to protect your organization’s security
Third-party vendors and contractors often require access to your systems to perform their tasks. This access may be necessary; however, it also poses inherent external threats. In the best-practice detection and monitoring of the insider threat, monitoring third-party access is paramount.
But how? Third-party users may be exposed to confidential information, introduce malware, or use others' login credentials. Sometimes, the cybercriminal might steal their login details and, hence, use their account without their consent.
You will be able to detect unusual activities or security policy violations through monitoring their access. For instance, if a contractor accesses systems outside their working hours or downloads large amounts of data, it may indicate a potential threat. Monitoring will help you spot these activities early, reducing the risk of harm.
How to monitor your third-party access?
- Implement role-based access control to limit the usage of third-party users to the available resources.
- Invest in a centralized access management tool that allows you to control and monitor third-party access all within one place, providing visibility into who accessed what, when, and for how long.
- You can implement multi-factor authentication (MFA) for access to authenticate with at least one additional factor for a successful login in a third-party access scenario, thereby reducing the chance of stolen credentials for fraudulent access.
4. Conduct event auditing for enhanced insider threat detection
Event auditing is a powerful method to enhance insider threat detection. It involves tracking and recording key activities across your organization’s systems. This includes logins, file access, data transfers, and configuration changes. By keeping a detailed log of these events, you can identify unusual patterns or behaviors that might signal a threat.
This best practice provides comprehensive visibility into how systems are being used. For example, if an employee suddenly downloads large amounts of sensitive data or accesses restricted files, event logs will capture these actions. Auditing tools can then flag these activities for further investigation.
Event auditing helps you pinpoint risks early and respond before any harm is done. It also creates a reliable trail of evidence, which is critical for compliance and incident response. Regular audits not only detect malicious intent but also highlight errors or oversights that could lead to security breaches.
5. Use a suitable insider threat management and security solution
Insider threats can be complex and hard to detect without the right tools. A dedicated insider threat management and security solution is a best practice for effective insider threat detection. These solutions are designed to monitor, analyze, and respond to suspicious activities within your organization.
A reliable insider threat solution continuously monitors user behavior and system activities. It relies on advanced technologies, including machine learning, to detect real-time anomalies. For example, if an employee accesses sensitive data at unusual hours or transfers files in an unusual manner, the solution raises alerts.
This best practice gives you insights into the risks and their mitigation in the shortest amount of time. It has reduced manual effort through automation, including detection and response, while also ensuring faster responses. It also helps fulfill compliance requirements with detailed log files of all activities.
Tips to Prevent Insider Threats in Your Organization
Now, let's learn a few tips to prevent insider threats in your organization.
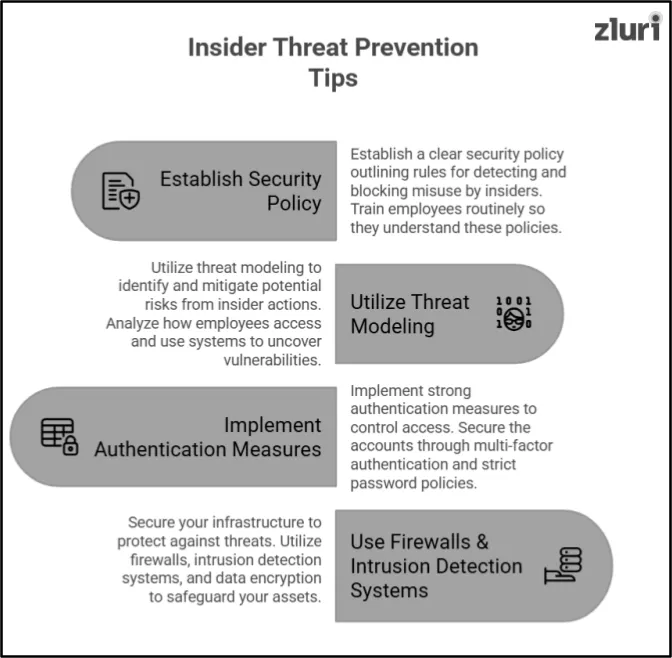
1. Establish a Strong Security Policy to Mitigate Insider Threats
A clear security policy is the foundation of insider threat prevention. This policy outlines rules for detecting and blocking misuse by insiders. Identify the approved use of systems and devices, along with the consequences for breaching policy. Train employees routinely so they understand these policies. Where your employees know what is expected of them, inadvertent or even intentional misuse of resources is minimized.
2. Utilize Threat Modeling to Identify Potential Insider Risks
Threat modeling helps identify and mitigate potential risks from insider actions. Analyze how employees access and use systems to uncover vulnerabilities. Create scenarios to understand how data might be misused or compromised. Develop controls to prevent these risks. By anticipating potential threats, you can stop insider issues before they occur.
3. Implement Strong Authentication Measures to Control Access
The primary defense against unauthorized access is authentication. Secure the accounts through multi-factor authentication. Implement strict password policies to ensure employees use unique and complex passwords. Monitor and review access rights regularly, and remove any unnecessary permissions. That's how insiders can be prevented from gaining unauthorized access to critical systems or sensitive data.
4. Secure Your Infrastructure to Protect Against Threats
It is challenging for an insider threat to exist in the presence of a robust IT infrastructure. Utilize firewalls, intrusion detection systems, and data encryption to safeguard your assets. Also, maintain up-to-date software and hardware with the latest security patches to address vulnerabilities. There should be a separation of access to sensitive systems, ensuring the system is not exposed. Insiders will find it difficult to exploit a secure infrastructural setup. This reduces the likelihood of data breaches.
Automate Your Insider Threat Detection to Enhance Security
Despite implementing preventive measures, insider threats can slip through. Malicious intent or human error can evade traditional detection tools. You may notice unusual system activity or unauthorized access attempts too late. By then, the damage might already be done. This is why a robust detection and remediation system is essential.
Moreover, detecting insider threats post-incident requires comprehensive visibility into your organization's access landscape. Identifying who accessed what, when, and how becomes crucial. Any gaps in this visibility can leave you blind to malicious activities. Furthermore, manually tracking suspicious patterns or behaviors is almost impossible.
To effectively address these challenges, you need an automated solution. The solution should detect risky access and help you respond quickly. Without this, your organization remains vulnerable, even after the initial threat has been addressed.
One such solution is Zluri. Firstly, Zluri helps you integrate seamlessly with over 300 SaaS applications in your environment. This integration helps you connect with your existing apps easily and provides you with insights into who has access to what tools and data.
Zluri offers an access review solution that simplifies monitoring your organization’s user permissions. It allows you to review and audit access across your organization. With its advanced capabilities, you can easily identify users with unnecessary or risky access. This is especially critical when dealing with potential insider threats.
One of Zluri's standout features is its auto-remediation capabilities. Once a risky access is detected, Zluri automatically addresses it. This eliminates the need for manual interventions, saving you time and reducing errors. By proactively remediating risks, you can prevent insider threats from escalating.
Overall, Zluri helps you detect, manage, and eliminate these risks. Its ability to integrate, review, and auto-remediate ensures that your organization stays secure.
Frequently Asked Questions (FAQs)
1. What are the various insider threat indicators?
Some of the insider threat indicators include:
- Privilege escalation
- Excessive downloads
- Frequent failed access attempts
- Unauthorized use of applications
- Odd login suspicious behavior
2. What is intellectual property theft?
Intellectual property theft is when one steals an idea, creative expression, or invention from a person or a company. IP theft can refer to patents, copyrights, trademarks, or trade secrets being stolen by someone.
3. What are the risks of insider threats?
Probably one of the largest risks that could be incurred by insider threats is that of a data breach. Since insiders have the privilege to access sensitive information, they can easily exfiltrate valuable data, which then leads to the Exposure of confidential customer information. Theft of intellectual property.









.svg)



























.webp)







.webp)
.webp)





.webp)